
Microsoft has long been a top, perhaps the top, cybercriminal target. Not only is its software ubiquitous, but many hackers just plain don't like the company. And perhaps most important, attacks on Microsoft give hackers one thing they seek most – publicity.
There is no end to zero-day attacks. Lessen the pain by spotting them early.
In recent days two zero-day vulnerabilities against Microsoft on-premises Exchange Servers have been publicized and exploited.The good news is that Exchange cloud users such as Microsoft 365 customers, need not worry as these exploits are only against the on-premises versions.
“Microsoft is aware of limited targeted attacks using two reported zero-day vulnerabilities affecting Microsoft Exchange Server 2013, Exchange Server 2016, and Exchange Server 2019. The first one, identified as CVE-2022-41040, is a server-side request forgery (SSRF) vulnerability, while the second one, identified as CVE-2022-41082, allows remote code execution (RCE) when Exchange PowerShell is accessible to the attacker. Refer to the Microsoft Security Response Center blog for the mitigation guidance,” a Microsoft blog
explained. “CVE-2022-41040 can enable an authenticated attacker to remotely trigger CVE-2022-41082. However, authenticated access to the vulnerable Exchange Server is necessary to successfully exploit either vulnerability, and they can be used separately.”
Microsoft has been tracking these exploits since mid-summer, and “observed activity related to a single activity group in August 2022 that achieved initial access and compromised Exchange servers by chaining CVE-2022-41040 and CVE-2022-41082 in a small number of targeted attacks,” the Microsoft blogsaid. “These attacks installed the Chopper web shell to facilitate hands-on-keyboard access, which the attackers used to perform Active Directory reconnaissance and data exfiltration.”
Microsoft has “medium confidence that the single activity group is likely to be a state-sponsored organization.”
The Microsoft diagram below shows how the chained exploit works.
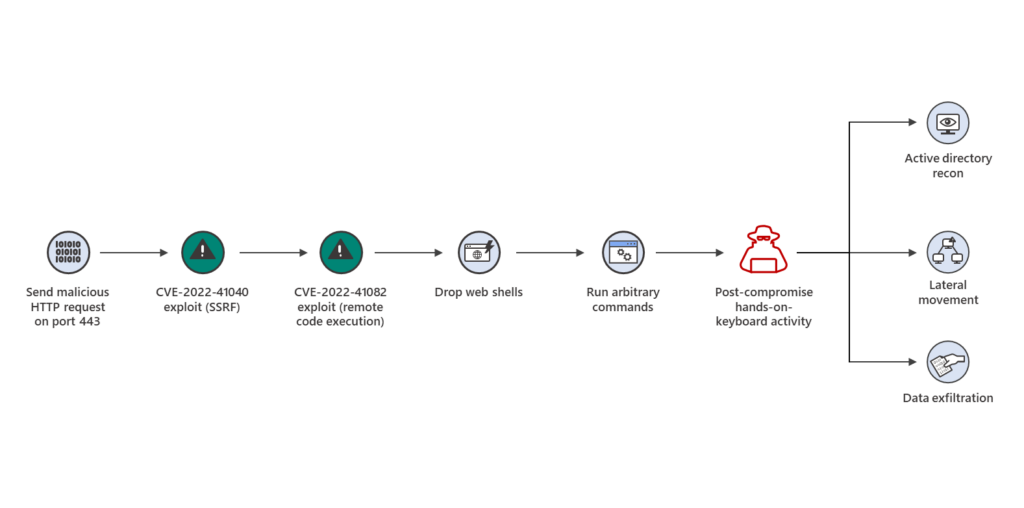
Diagram of attacks using Exchange vulnerabilities CVE-2022-41040 and CVE-2022-21082.
Public Disclosure Ups the Ante
Cyberattacks explode once there is public disclosure, and that is just what happened after September 28, 2022 when GTSC published a blog breaking the news of the exploit. “It is expected that similar threats and overall exploitation of these vulnerabilities will increase, as security researchers and cybercriminals adopt the published research into their toolkits and proof of concept code becomes available,” Microsoft cautioned.
Patching/Updating
Once a vulnerability is disclosed, attacks are no longer zero day. And once patches or updates are released to close the hole,attacks generally increase and become more dangerous. Two reasons.The public disclosure, as well as the patches or updates, create a blueprint for cybercriminals who spring into action exploiting the vulnerability. Often attacks are shared and even sold as services, so even the most amateur of hackers can go after networks. That is why it is vital to patch or update your systems as soon as security fixes are available — otherwise, your network is a sitting duck.
Phishing for Admins
Elevation of privilege attacks allow hackers to gain access to the deepest reaches of the network. One shortcut is to take over the admin accounts themselves – often through phishing. For example, an IT admin may get an e-mail tricking them into disclosing their credentials.
Here is an example of a phishing attack against Office 365 administrators — though it can happen to any IT pro.
In other cases, IT admin accounts are all too easy to crack as far too few use multi-factor authentication (MFA). In fact, Microsoft surveyed attendees at its Ignite conference, finding a shocking less that 2% of all Office 365 global admins have MFA enabled.
Meanwhile, results of a survey by CoreView were better, but still stunning – 78% of O365 admins do not have MFA activated. At the same time, 57% of these administrators have excess, elevated permissions and privileges that let these admins and the hackers who steal their credentials access, modify and steal critical data.
Yes, this does sound stupid, but admins often have many,many accounts and that extra step to log into each is clearly a nuisance. You know what is more annoying? Having a hacker steal privileges and put your very enterprise at risk!
While these are cloud examples, one can assume MFA and excess privileges are just as bad on-premises.
Anomaly Detection/Network Behavior Analysis (NBA)
The definition of a zero-day attack is onethat anti-malware/anti-virus solutions and other security tools have not yet defined – and therefore cannot defend. Since it is difficult to block these attacks, it is vital that IT know of incursions as soon as possible. That requires a deep understanding of what is happening on the network, the ability to spot unusual activity immediately and at the same time define where that activity is happening. The key here is network behavior analysis (NBA), also known as anomaly detection.
So what is network behavior analysis? “Network behavior analysis is a network monitoring program that ensures the security of a proprietary network. NBA helps in enhancing network safety by watching traffic and observing unusual activity and departures of a network operation,” explained Techopedia. “Network behavior analysis monitors the inside happenings of an active network by collecting data from many data points and devices to give a detailed offline analysis. It is constantly watching the network, marking known and unknown activities, new and unusual patterns and indicating potential threats by flagging. Network behavior analysisalso checks and accounts for change in bandwidth and protocol being used during communication. This is particularly applicable in finding a potentially dangerous data source or website. The duty of a network behavior analysis program is to reduce the labor and time expended by network administrators in detecting and resolving network issues. It is thus an additional layer.
Take Gartner’s Advice
Gartner believes an NBA is a critical security step. “After you have successfully deployed firewalls and intrusion prevention systems with appropriate processes for tuning, analysis and remediation, you should consider NBA to identify network events and behavior that are undetectable using other techniques,” said Paul Proctor, VP at Gartner.
NBA Strengthens Defense In-Depth
As Gartner indicates, network behavioranalysis(NBA) is an essential part of your defense-in-depth arsenal and bridges the gap between end point and perimeter protection by residing within the network. An NBA does not rely upon signatures to detect attacks but instead analyzes network behavior to spot things that are out of the ordinary and indicative of an attack. Not only that the NBA spots where the unusual behavior is occurring and what systems are involved.
With an NBA, IT is alerted to a hacker incursion and can respond quickly. This is due to in-depth monitoring and analysis of the entire network. “The rise of unknown malware compromising internal systems, devastating DDoS attacks, APTs and threats bypassing traditional security have changed the IT security landscape. Building perimeter walls and relying on signature-based solutions is not enough anymore. Only a detailed awareness of network behavior and a proactive fight against cyber threats can give control over the IT environment back to administrators,” argues Flowmon’sNetwork Behavior Analysis and Anomaly Detectionpage.
Learn More About How Flowmon Helps
Flowmon ADSand Network Behavior Analysis help IT determine what is abnormal activity on your network, reports these anomalies and detects intrusions and attacks not visible by standard approaches so IT can respond fast and minimize the financial impact.
“Flowmon delivers to businesses an advanced security intelligence based on NBAD technology. Its Flowmon Anomaly Detection System (ADS) is a powerful tool trusted by CISO and security engineers globally providing them with dominance over modern cyber threats. The solution utilizes sophisticated algorithms and machine learning to automatically identify network anomalies and risks that bypass traditional solutions such as firewall, IDS/IPS or antivirus,” the Network Behavior Analysis and Anomaly Detectionexplained.
Flowmon ADSalso includes reputation databases which help spot communication with known attackers, command control domains, botnets, peer-to-peer networks, spammers and more.
Flowmon Proves Zero-Day Mettle
Flowmon reseller Propellent used to rely on an intrusion detection system working in tandem with a firewall for triggered IP address blocking. While certainly effective against many types of attacks, this system was time consuming to fine-tune and would not scale very well into the future. It also only gave perimeter coverage of network-borne threats.
“But the real issue was not day-to-day management,” says Matt Wanless, Managing Director at Propellent. “The previous solution offered good defense against known threats, but when it came to zero-day attacks or advanced persistent threats, we had to rely on endpoint protection to protect our clients, which we found to be a costly and time-consuming approach, and still had significant limitations.”
With that success, Propellent moved to offer Flowmon as a managed service to, among other things, mitigate Zero-Day threats.
Not long after the Flowmon product suite was added to Kemp’s portfolio, we approached Propellent, who had thus far been a reseller of the LoadMaster line of load balancers and introduced the Flowmon solution to them.
“We wanted to give it a proper test, and so we implemented it on a small scale under an NFR license first,” continues Wanless. “It was important to do a real-world assessment of Flowmon, so in conjunction with one of our customers, we test-deployed it against some of their live services.”
This was imagicam, one of Propellent’s customers to whom they provide hosting and managed security.
“imagicam is dedicated to protecting data and using industry best standards. We understand the importance of data security and make every effort to ensure that data held on the systems is fully protected,” says Peter Grey of imagicam.
Through Propellent, imagicam utilize a defense-in-depth approach using best-of-breed technology and processes.
“The outcome was a nice concise view of all the threats in imagicam’s infrastructure that allowed easily actionable intelligence,” says Wanless. In this way, Propellent gained an unquestionable source of truth on network-borne threats endangering the customer and were able to test and demonstrate the product’s capabilities with real traffic data.
The deployment consists of a virtual Kemp Flowmon Collector with the Anomaly Detection System (ADS) module for network-based behavior analysis and anomaly detection. The system uses an Open vSwitch and flow data from other switches as a source. “This, too, was a win for us,” adds Wanless, “as we could use what we had as sources of flow data instead of being pushed to buy proprietary sensors straight away.”
Propellent appreciates the ease of management, streamlined event investigation workflow and the ability to add additional tooling into the event view in ADS to integrate their own bespoke tooling.
Learn more in our Propellent Provides Managed Zero-Day Threat Protection with FlowMon case study.
Leave Attackers Nowhere to Hide
Even if your servers are compromised by a Microsoft exploit, Flowmon’s network security means those attackers stand no chance. Its state-of-the-art Anomaly Detection System allows Flowmon to detect lateral movement, data exfiltration or other attacker’s malicious activity on the network.
Find out more about Flowmon Anomaly Detection on our website.
Doug Barney
Doug Barney was the founding editor of Redmond Magazine, Redmond Channel Partner, Redmond Developer News and Virtualization Review. Doug also served as Executive Editor of Network World, Editor in Chief of AmigaWorld, and Editor in Chief of Network Computing.