A Close Look at 3 Use Cases in Flowmon Packet Investigator 11.1

About 3 months ago, I spoke to one of our customers, an employee of an unnamed government entity, about Kemp Flowmon Packet Investigator (FPI). After giving him a short demonstration, he told me a story that happened to him just a couple of days earlier.
“As part of my job,” he told me, “I need to analyze PCAP files when they come and look for different types of traffic.”
“The other day I received a PCAP file from my colleague John with the request to find ‘traffic X’. So, I open the PCAP and get into it. After spending 2 hours looking for what obviously was not there, I went back to John and told him ‘There is nothing inside!”
“And John just casually looked at the file and said, ‘I am so sorry, I accidentally sent you the wrong file.”
“If I had had the Flowmon Packet Investigator then, I could have known immediately what was in the PCAP and saved myself 2 hours of work.”
Flowmon Packet Investigator (FPI) is an on-demand packet-capture solution specifically designed to help you find the root cause of a problem in cases where traditional flow monitoring is not enough, while saving you the bother of going through a ton of data with traditional full packet capture and analysis.
FPI investigates data by looking for RFC deviations in a number of different protocols (e.g. DHCP, DNS, FTP, IMAP, IMP, POP, SIP, SLAAC, SMB, SMTP, IP, TCP, SSL, HTTP, and more), but in addition to immediately giving you a list of the protocols used, it also highlights the errors and offers you a possible explanation of their cause.
Now, let’s take a look at several examples.
Missing encryption
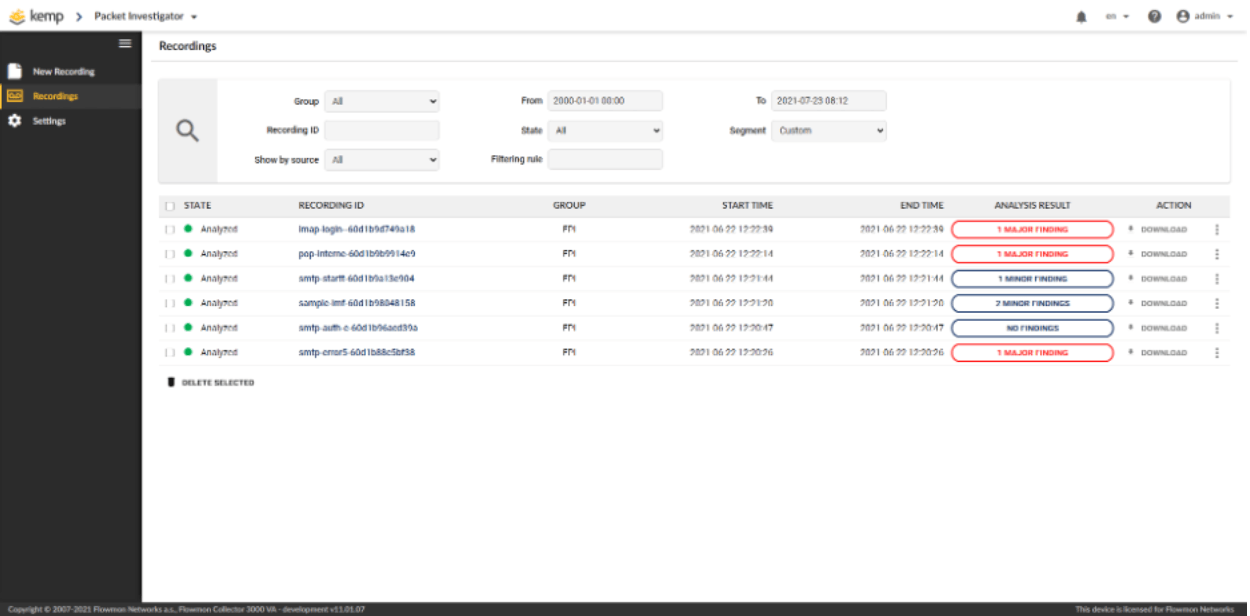
Here is a sample of captured traffic (figure 1), which is ready for analysis. The new FPI 11.1 gives you a clear overview of all the captured PCAPs designated by a recording ID where you can see the protocols and the outcome of the analysis.
Figure 1 – FPI PCAP overview
Looking at the outcome of the analysis (figure 2), you can see straight away every important detail of the captured data organized in a decision tree.
Figure 2 – PCAP analysis SMTP protocol 1
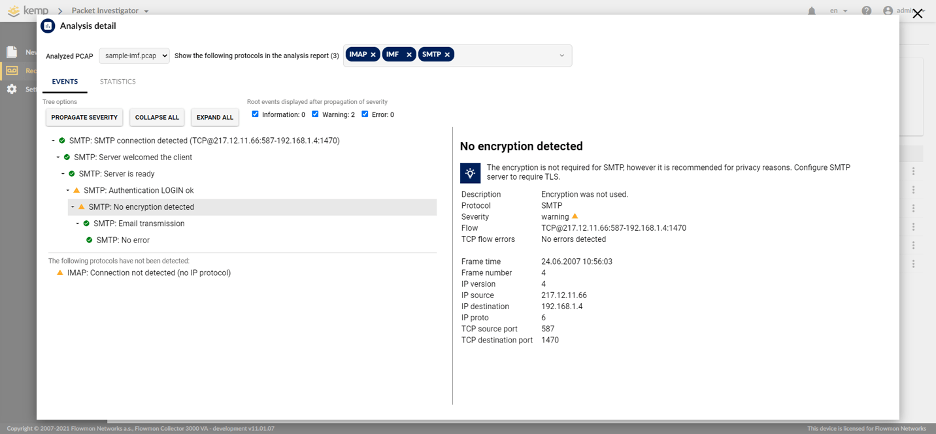
Starting at the top, you can see the SMTP protocol with green check marks, which means that the client initiated a communication with the server, which responded “server is ready” to communicate.
Next, the client sent its authentication (login) without encryption, which you can see as plain text in the detail description. This is immediately caught by FPI and marked with a yellow warning sign “No encryption detected.”
This is a potential security risk; if anyone were listening to the traffic with malicious intention, they could easily obtain this information and exploit it.
Next, you can see that the email communication was sent and received by the server without any errors.
If you were to investigate this PCAP file manually, for example in Wireshark, you could easily overlook the missing encryption even if you are an experienced IT professional, because at the first sight, there is no apparent problem.
Oversized attachment
Let us look at another PCAP, this time analyzing a transaction error (figure 3).
Again, you can see a communication between a client and a post server. When you click on the SMTP error message, you can see a proposed solution, “Try to send a lighter message. This usually happens when you dispatch emails with big attachments, so check them first.”
Figure 3 – PCAP analysis SMTP protocol 2
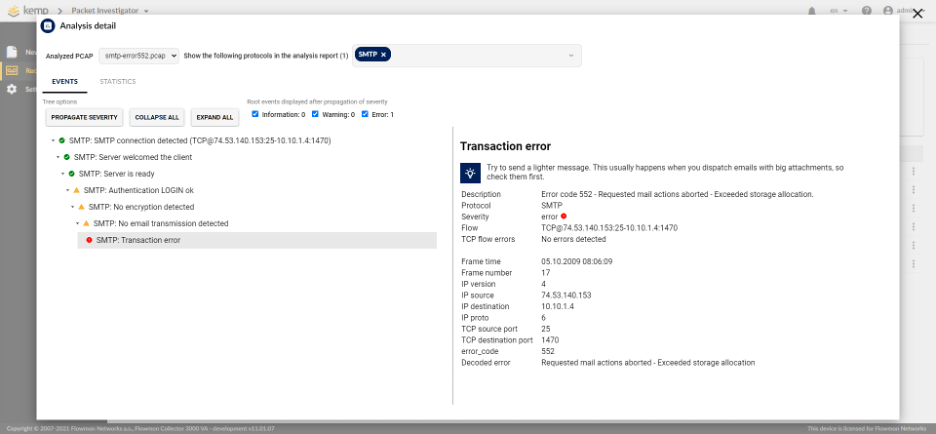
In addition, you can see an error code 552 – exceeded storage allocation in the description.
A clear simple, and easy explanation of what the problem is.
Incorrect address
Finally, let’s take a look at the last PCAP file containing an email communication that shows how the FPI detects errors (figure 4).
Figure 4 – PCAP analysis IMAP protocol
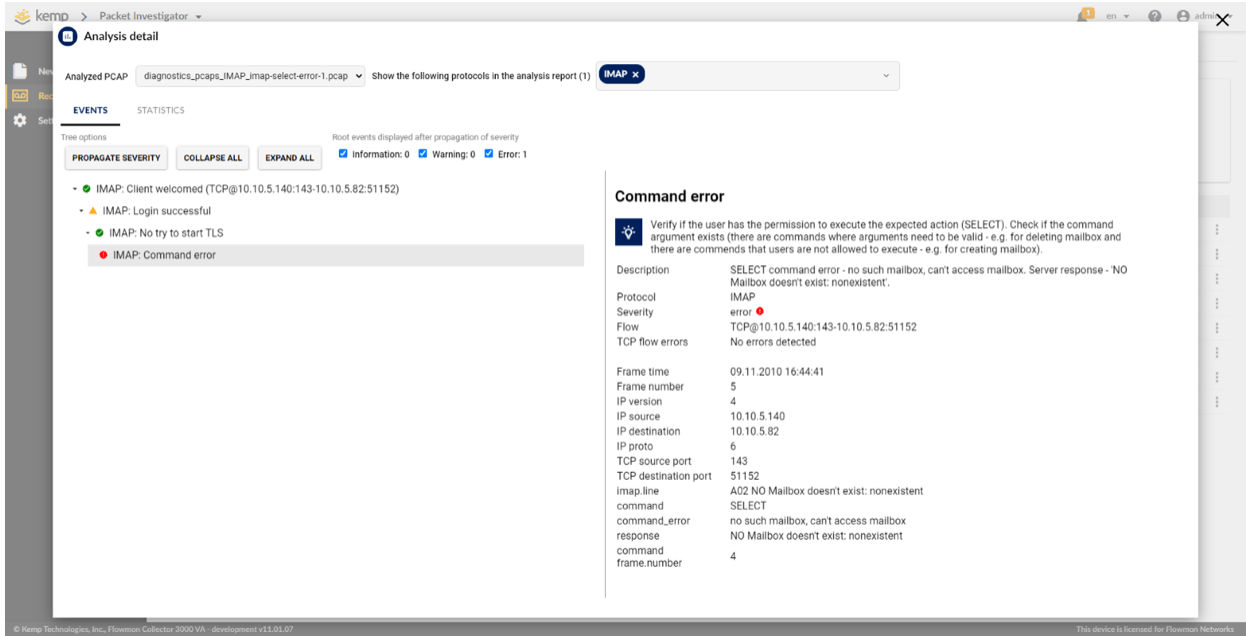
Diving into the intelligent decision tree analysis of the PCAP file, you can clearly see the established communication between clients and server as well as a successful login.
But then, the TLS communication fails to start, followed by a command error message, marked with a red icon. Looking closely at the description, you will notice the “mailbox doesn’t exist” message, indicating an incorrect email address.
This is how remarkably simple it can be to track down and understand the root cause of problems in FPI.
Flowmon Packet Investigator is a simple and elegant solution built for IT engineers who need to troubleshoot network issues on a daily basis. The FPI provides them with a clear and simple analysis that not only saves their time but provides a helpful suggestions of remedial action for those who happen to lack the necessary knowledge and experience to make sense of the data manually.
