Apply monitoring of AMT attack for your datacenters and users

The attack to Intel based hardware is still going on via Intel® Active Management Technology.
More than one month known critical vulnerability CVE-2017-5689 (CVSS score 9.8) is not patched fully yet by new BIOS versions and we are not fully focused on the risk as new threats like WannaCry or SambaCry are coming in last weeks.
The bug has been lingering in Intel platform for 7 years and it is really hard to say how many systems and computers are affected by the vulnerability. Not all systems with Management Engine are automatically vulnerable. According to Shodan, the AMT service is open to internet on more than 5000 systems. Shodan indexes the internet for devices and open ports and of course it is only top of an iceberg and the reality behind firewalls is even worse.
There can be some possible backdoor still opened for attackers on ports 16992-16995, 623, 664 and the vulnerability is not patched by operating system, because the fault is on the hardware level. This vulnerability can be finaly used for malicious file transfer by hacking tool developed by Platinum group although the card is disabled in operating system.
To prevent from this vulnerability, we have described detection of harmful communication which can be setup by Custom pattern definition in Flowmon ADS and applied for your critical network segments:
destination_port IN (16992, 16993, 16994, 16995, 623, 664) AND protocol = 6
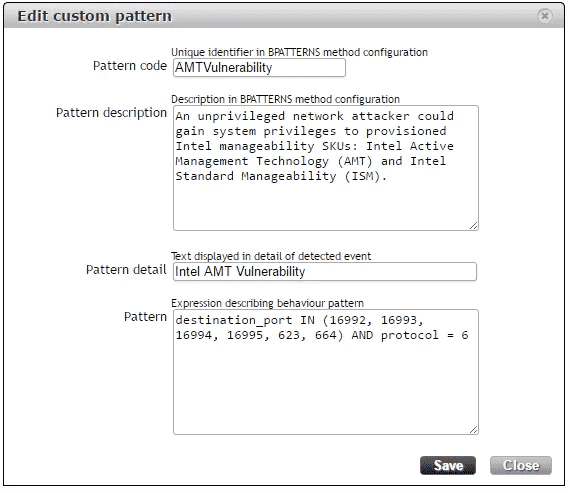
The recommended next step action is to scan your infrastructure by vulnerability scanner (e.g. by Nessus), or use directly Intel mitigation tool for Windows and Linux.
The Flowmon hardware is not affected by this vulnerability at all as the Intel® Active Management Technology is not used for server management.
Using custom behavior patterns it is possible to detect various operational issues and security anomalies. If you want to know, how user defined behavior patterns help with WannaCry ransomware detection, check this previous blog post.
Tomáš Vlach

Latest Stories in Your Inbox
Subscribe to get all the news, info and tutorials you need to build better business apps and sites