Catch Cyberattacks Through Reliable Network Detection

In today’s rapidly evolving cyberthreat landscape, organizations require network detection solutions that help identify and mitigate threats before significant damage is done. Among the options available on the Network Detection and Response (NDR) market, Progress Flowmon Anomaly Detection System (ADS) stands out for its unparalleled ability to detect threats throughout every stage of an attack.
Real-World Cyberattack Detection Testing
Progress simulated three different cyberattacks that affect organizations to help us truly understand the capabilities of network detection products.
Case 1: Man-in-the-Middle Attack
An adversary spoofs network traffic to act as a middleman to steal credentials, gain access to the victim’s PC, install fake certificates and ultimately receive access to the encrypted communications.
Case 2: Ransomware Attack
A compromised PC uses a keylogger to collect credentials and search for network storage. The PC exploits RDP protocol BlueKeep (CVE- 2019-0708) vulnerability to obtain access to company data. The PC exfiltrates sensitive data in smaller chunks from the company network. The data is encrypted and the adversary asks for a ransom. Explore the full ransomware use case in our guided demo example.
Case 3: Supply Chain Compromise
An adversary scans the internet for a vulnerable version of a Help Desk system and receives access to the company network. Using a backdoor, the adversary immediately scans for potential victims on the network focusing on available services and systems. The adversary exploits SIGRed (CVE-2020-1350) vulnerability to get access to the Windows server. Then it disables Windows Defender to avoid detection, exfiltrates data using DNS tunneling and exploits NTFS vulnerability (CVE-2021-28312) to corrupt file system.
The results were clear: only Flowmon ADS could consistently detect anomalous behavior across all phases of the attacks. What were the results of other competitors? For example, "Vendor A" did not detect unusual DHCP and DNS traffic, indicating adversaries’ attempts to reroute the traffic and act as a man-in-the-middle. While the second scenario returned comparable results, the third missed detection in the discovery phase (ARP scanning), collection, exfiltration and impact phases (data collection and exfiltration and clients unable to access network storage due to the server’s corrupted file system).
The competitors’ detection capabilities sometimes didn’t cover specific anomalies. For example, the lack of ARP scan detection was commonly observed during the testing. ARP scans are early indicators of malicious activity. With Flowmon ADS, raising awareness earlier in the cycle, you can act quickly to mitigate these malicious threats.
Another pain point is the ability to tune the systems. While Flowmon ADS allows customers to tune the sensitivity to adjust the learned thresholds and tailor the accuracy of detection, competitors solutions are usually black boxes. This can result in anomalies not being detected and leaving gaps in the ability to detect complex cyberattacks throughout their whole lifecycle.
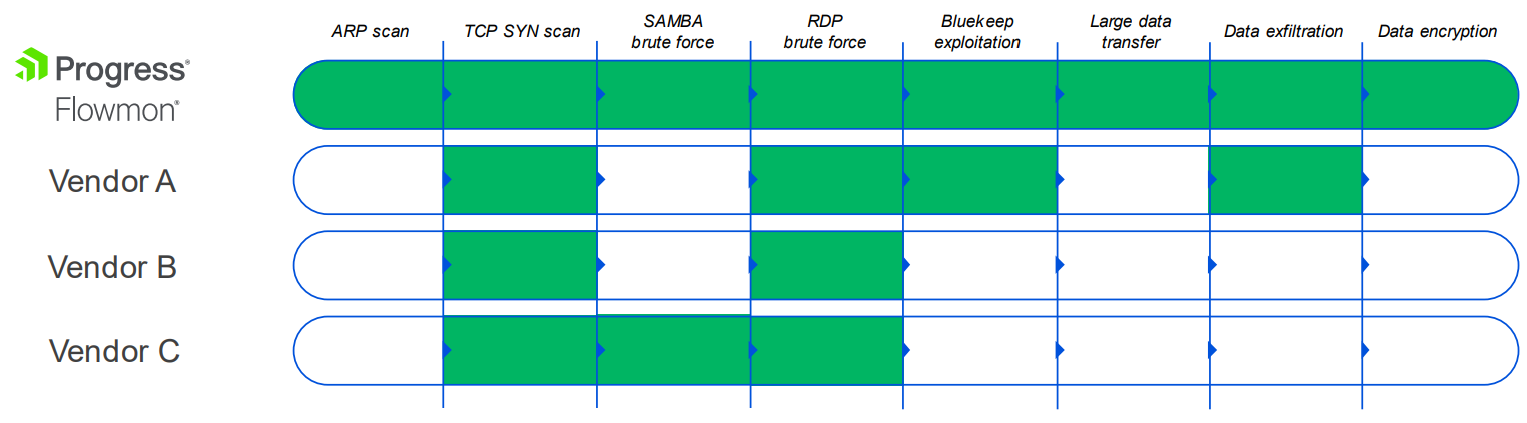
The holistic network detection approach Flowmon ADS brings sets it apart in the cybersecurity market. While other competitors could detect alerts in various attack phases of afore-mentioned real-world scenarios, only Flowmon ADS provided comprehensive coverage across the entire cyberattack lifecycle. This detection capability means that organizations can rely on Flowmon ADS to help them safeguard their networks at every stage of an attack, reducing the risk of breaches and facilitating swift, effective responses. With Flowmon ADS, security admins gain comprehensive visibility, allowing them to prioritize issues more effectively, achieve a deeper understanding of threats and respond more swiftly.
