Data Protection is Not Complete Without a Secure Managed File Transfer (MFT) Software
Data threats are increasing every day and smart IT pros are racing to not just keep up but get ahead. One area many neglect is secure file transfer.
Are these files encrypted? Do you know where they are going and to whom? Before we dive deeper into file transfer, let’s pick Osterman’s brain about the data threats it examined in its “What Decision-Makers Can Do About Data Protection” report.
Type of Data That Have Been Breached
A picture tells a thousand words, and so does a graph. Below you see what kind of data is regularly breached, and how often an organization's defenses are overrun.
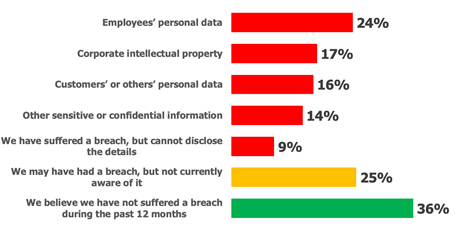
Source: Osterman Research, Inc.
And where is much of an enterprise’s prized data held? In files, of course! The top three categories of breached data types each represent a disaster if compromised. Employees’ personal data leaves your company liable -- and with egg on its face. Intellectual property is your lifeblood – assets your competitors and cybercriminals would love to have. And customers' personal data – that may be the worst, most damaging and most embarrassing to lose.
Where do Breaches Come From? Employees Many Times
Your employees know where the most valued data lies, and often how to get it. “Employees are a frequent cause of data loss for organizations. So-called insider threats include inadvertent data loss from mistakes and negligence, as well as malicious data loss by disaffected employees undertaken due to a range of motivations. For organizations paying attention, however, the signs of upcoming data protection issues can be seen in advance,” Osterman argued.
Verizon has been tracking employees and other insiders for years and is a noted authority on the subject. “An insider threat is a threat that comes from inside your organization. It is usually someone who uses their authorized access—intentionally or unintentionally—to compromise your organization's network, data, or devices. The critical part is that the access is legitimate—these aren't brute-force hackers,” Verizon argued in its The Risk of Insider Threat Actors blog. “As the Verizon 2020 Data Breach Investigations Report notes, external actors remain the most significant threat to organizations, despite widely held opinions to the contrary. Still, the insider threat cannot be ignored. The report indicates that more than 30% of breaches in 2019 were the work of insiders.”
Employees and other insiders often cause the biggest problems. “Outside actors need an exploitable weakness to get inside a network; insiders are already there. They don't need to hack the enterprise or circumvent its defenses because they have legitimate access to endpoint systems, servers, networks and domains, and they often need that access to perform their daily duties. Insider threat actors recruited or bribed to steal sensitive company data are just as dangerous as disgruntled employees seeking to disrupt business or access information for personal gain,” the Verizon blog noted.
Breaches on the Rise
Data breaches have existed as long as there has been data, but instead of pilfering through a file cabinet, thieves rummage through your computer files. “Data breaches are on the rise, with the first quarter of 2020 witnessing a higher number of breached records than the combined count of breached records for the first quarters of the previous seven years. One mega-breach in the first quarter of 2020 exposed more than five billion records, and hardly a day goes by without yet another breach notification by an organization or cyber-attack alert against a country by a nation-state actor, and industries that have already been pegged as highly attacked are reporting ever-increasing attack activity,” Osterman found.
Discover what data protection is all about from the experts at Osterman in the What Decision-Makers Can Do About Data Protection guide!
Compliance Ups the Need for Data Protection
If your company is breached, it is a big problem. If your company falls under compliance rules, it is an EXPENSIVE problem. “A growing panoply of privacy regulations around the world is contributing to the drive for heightened data protection approaches. GDPR, CCPA, HIPAA, PCI-DSS, and others impose requirements on how personal and sensitive data is handled by organizations, and the principle of extra-territoriality redraws the lines of jurisdictional applicability,” Osterman warned.
Compliance rules are growing in number and enforcement is getting stricter. “Privacy is a global trend, and a growing set of regulatory mandates place significant obligations on organizations to protect data; obligations that carry severe financial penalties if ignored or not met. Europe’s GDPR, California’s CCPA, HIPAA for the healthcare industry in the United States, New York’s NYDFS Cybersecurity Regulation for financial institutions operating in New York, and other existing and new data protection regulations around the world elevate the importance of data protection by design, introduce specific data breach identification and notification requirements, and transform penalties from being a mere slap on the wrist. New privacy regulations re-think the rules of jurisdiction, focusing on where the data subject is located rather than where the organization collecting or processing personal and sensitive data is based,” Osterman explained.
How Secure Managed File Transfer (MFT) Software Helps
Many data breaches occur when files are moved within your organization or to partners and other organizations with a vested interest. These breaches come with GDPR investigations and often crippling fines. With MOVEit Managed File Transfer (MFT) from Progress, you can establish secure collaboration and automated file transfers of sensitive personal data. These files are not only moved safely, but they also include encryption and activity tracking to ensure compliance with GDPR, as well as PCI and HIPAA.
By default, all files sent outside of the company should be handled in a secure and trackable way – which is MFT.
With MOVEit Managed File Transfer, you no longer rely upon your employees emailing personal data to other employees or outside entities, or using insecure file sharing services. With Secure MFT Software, you eliminate user error and can track and report the details of every file transfer.
Shadow IT - the Exact WRONG Way to Transfer Files
Many think DropBox and other file-sharing apps are cool – and they can be. For simple sharing of non-sensitive files, they are great. Just not for enterprises and the sensitive data they contain. Unfortunately, many enterprise employees use the DropBoxes of the world to send around YOUR data.
These unauthorized apps are a breach and compliance fine waiting to happen. “Shadow IT services, the use of personal devices, the adoption of a 'cloud-first' or 'cloud-only' strategy, and merger and acquisition activity, among others, represent a collection of other threats to data protection. Decision-makers must evaluate the relevance and magnitude of these threats and develop appropriate countermeasures,” Osterman argued.
Those that fail to stop Shadow IT pay the price. “The use of Shadow IT apps and cloud services results in confidential data being stored in systems with unknown security protections, the usage of apps that were never designed with business purposes in mind, and threats of unpatched and unidentified software vulnerabilities leading to data breaches. As employees embrace cloud applications beyond the list of corporate sanctioned services, inadvertent and malicious data leakage increases, along with unauthorized access to sensitive corporate data,” Osterman cautioned. “Shadow IT services that are not connected to the identity and authentication solution of the organization can also support malicious insider data theft. For example, revoking a user’s identity on their departure or termination will prevent future access to services connected to the identity solution, but for non-connected shadow IT services, no such prevention is possible. An ex-employee can continue to log in and access current and new data stored and shared through these services.”
Develop a Data Protection Plan
The A-Team loves it when a plan comes together – and they always had a plan. You need one too if you are to properly protect your most cherished data assets. “Addressing the data protection challenge requires proactivity by decision-makers. Engage the board, conduct a thorough audit across the organization, implement best practices, and use training and technology to strengthen defenses, elevate protections, and mitigate the major data protection risks facing your organization,” Osterman advised.
Conduct Research on Sensitive Data
Your plan should begin with a discovery process. “What types of sensitive data are created, received, stored, and processed across your organization? Where is it supposed to be held, and what protections are in place for those authoritative systems? Where is sensitive data not supposed to be, and how many instances can you find of sensitive data in the wrong place without appropriate protections in place? Are there particular people or groups who should have access to your sensitive data? How tight are the access controls for this data, and who has access who should not have access?” Osterman asked.
Did you know that documents, and Microsoft Office docs in particular, are where MOST of your company’s sensitive data is held? “Sensitive data is often stored in carefully protected systems with access controls and restrictions on usage. However, once data is exported from these systems – sometimes for valid business uses such as customer segmentation or powering a marketing campaign – it’s easy to lose control over the data. Sending sensitive data in email messages or as attachments, results in a broader attack surface for sensitive data, thus increasing the threatscape if an email account or cloud storage account is compromised,” Osterman said.
Implement Best Practices
Now that you have a plan, and know where the secrets lie, it is time to implement best practices.
“Access to corporate data repositories should be carefully managed, using a mixture of general access permissions, conditional access rules to take account of risk-based attributes for each access session, and multi-factor authentication if the characteristics of the access attempt warrant it,” Osterman suggests. “Corporate data repositories should be used for corporate data only, and if backups are made, sufficient protections over backup devices enforced. Exporting data from corporate data repositories greatly increases the risk of inadvertent or malicious data usage and should be dissuaded wherever possible through the use of secure integrations between systems rather than ad-hoc integrations using CSV exports.”
Encrypt Encrypt Encrypt
Perhaps the BEST best practice is encryption, and that means adopting solutions such as Managed File Transfer with strong and easy to use encryption. “Identify solutions that encrypt data using techniques that maintain data format and referential integrity so that data can be used in its protected state without requiring decryption,” Osterman strongly advised. “Applications that use sensitive data – as well as databases, data lakes, analytic platforms and other repositories that use data in structured formats – benefit from field-level encryption to provide data-in-use protection for personal and high value data. Enforcing field-level encryption on sensitive 'crown jewels' data assets enables business usage to drive value for the enterprise without compromising data privacy mandates.”
External File Transfers Pose a Particular Data Risk
Your company needs to communicate with the outside world, and that includes sending important pieces of information in the form of files to external entities. Unfortunately, these files can be intercepted by cybercriminals, but also subject to other forms of unauthorized access or simple end user mishandling which opens the file up to those that should not see it.
Many companies try and secure external data transfers by creating policies that warn end users of the dangers, or they use file sharing solutions they believe to be secure, or even FTP (File Transfer Protocol) systems. None of these three offer the security that GDPR demands. The best option is a Secure MFT software such as MOVEit from Progress.
GDPR does not just ask for compliance, it requires your IT and security teams to prove compliance – with evidence. That is no problem with MOVEit Managed File Transfer, which tracks all file transfer activities, including authentication actions, in an archivable database.
With MOVEit Managed File Transfer, your end users can stop relying on insecure methods to share your company’s most precious and regulated information. Meanwhile, workflows and automated file transfer tasks accelerate your data sharing process while eliminating user error.
Learn About Data Protection from the Experts
Discover what data protection is all about from the experts at Osterman in the What Decision-Makers Can Do About Data Protection guide, then learn from Progress how MFT locks down sensitive data. In this guide, Osterman Research shares what security leaders should be focusing on and how to prepare your organization for total data protection.
In What Decision-Makers Can Do About Data Protection, you will learn:
- Areas of concern for decision-makers
- How to protect data loss by employees
- What decision-makers should do to protect data
- And More!

Doug Barney
Doug Barney was the founding editor of Redmond Magazine, Redmond Channel Partner, Redmond Developer News and Virtualization Review. Doug also served as Executive Editor of Network World, Editor in Chief of AmigaWorld, and Editor in Chief of Network Computing.
