Unifying Security and Data Recovery for More Seamless and Robust Cyber Defenses

Cybercriminals are constantly looking for ways to bypass defenses. You need to plan for when attackers will breach your defenses. When attackers exploit a vulnerability, you need a solution that quickly detects activities, mitigates attacks, expels attackers and enables recovery from any damage caused.
It’s becoming increasingly clear that having a unified approach to data security is essential. In a recent webinar, experts from Progress and Veeam discussed how Progress Flowmon detection solutions, combined with Veeam’s data protection and recovery solutions, work together to deliver a robust threat defense. Let’s look at the topics they discussed.
The Costs of a Data Breach
To kick off the webinar, Frank Cotto, Principal Solution Architect at Progress, shared data to highlight the damage that can be done when cyberattackers get access to a network for long enough to perform a data exfiltration. Frank said:
“In 2023, the average time to detect a data breach was 204 days, and the average time to contain a breach was 73 days. During a breach, the average cost of a data breach was estimated to be $4.45 million. However, organizations leveraging security AI and automation diminished the average cost by $1.76 million.”
Beyond the financial impact, organizations also grapple with a cascade of additional work. Recovery time can be extended as IT teams work to investigate the vulnerabilities that allowed the breach, recover damaged systems and implement new security measures to prevent reoccurrence. Depending on the industry and location, companies may also face hefty regulatory fines for non-compliance with data protection regulations. All of these could significantly affect their reputation.
However, it’s not all doom and gloom. As discussed in the webinar, organizations deploying security and data recovery tools that use machine learning and advanced automation significantly reduce the time taken to detect attackers and recover from an attack. Using tools with these features reduces the average cost associated with a data breach by $1.76 million. This significant reduction underscores the importance of adopting advanced, integrated security solutions such as those from Flowmon and Veeam.
Webinar
Check out the full 26-minute webinar led by Ivan Cioffi from Veeam and Frank Cotto from Flowmon.
Modern Cybersecurity Defense Infrastructure
Modern security architecture is a complex, multi-layered system designed to defend against various attack vectors. This approach recognizes that no single solution can provide complete protection. Instead, it relies on a carefully orchestrated combination of tools and strategies.
A core part of any fit-for-purpose cybersecurity defense strategy includes Network Detection and Response (NDR). NDR solutions, like Flowmon, constantly monitor network traffic activity for signs of anomalous behavior. When malicious activity occurs, NDR can detect and analyze the anomalous activity and alert the SOC (Security Operations Center) cybersecurity team. Then they can act in conjunction with other cybersecurity solutions, including SIEM (Security Information and Event Management) systems.
In addition to NDR and SIEM, an extensive cybersecurity defense strategy needs additional tools such as traditional border firewalls, intrusion prevention systems (IPS), web application firewalls (WAFs), multifactor authentication (MFA), privileged access management (PAM) and network micro-segmentation. Your strategy might require the adoption of frameworks such as zero-trust network access (ZTNA) plus software-defined wide area networking (SD-WAN). Finally, every organization needs to have trustworthy data backup processes like those delivered by Veeam, as these provide a powerful safety net for data recovery from malicious attacks such as ransomware.
Minimizing the Time Attackers Have to Steal Data
The average time to detect a breach is around 200 days, giving attackers ample time to discover and exfiltrate data from a breached network. However, using an industry-leading NDR solution from Flowmon can reduce the time between network compromise and detection from months to hours.
Once attack activity is detected, the next step is preventing lateral movement by the attackers or their software within the network. After defenders stop attackers, the next step is swift expulsion from the network and systems. With well-prepared incident response plans, teams can quickly isolate and remove threats from the network, cutting off the attacker’s access and preventing further damage.
After attackers get expelled, the next step is to repair any damage they caused. Sadly, in the current environment, the damage is often due to data encryption by ransomware. Paying a ransom to recover from an attack is not a viable option. Many organizations don’t want to reward criminal behavior, and in many jurisdictions, it’s becoming illegal to pay ransoms to cybercriminals. Additionally, evidence shows that many organizations that pay a ransom don’t receive a working way to recover their data.
The ideal data recovery process involves reliable backups that haven’t been impacted or infected during the cyberattack. Modern backup and recovery solutions like Veeam enable organizations to restore systems and data to a clean state quickly, minimizing downtime and data loss after an attack. Veeam’s rapid recovery capability delivers an essential service in today’s environment, where every minute of downtime can translate to significant financial losses.
Throughout the detection, cleanup and restoration process, continuous monitoring remains vital. By maintaining vigilant 24/7 monitoring from an SOC, organizations can detect any resurgence of the threat or new attack attempts, maintaining network security during and after an attack.
Breaking the Attack Chain with Flowmon and Veeam
The cyberattack chain, also known as the cyber kill chain, is a framework that outlines the steps or stages involved in a cyberattack. It characterizes a cyberattack in seven stages. Figure 1 shows the stages and where Flowmon and Veeam solutions can act to break the chain.
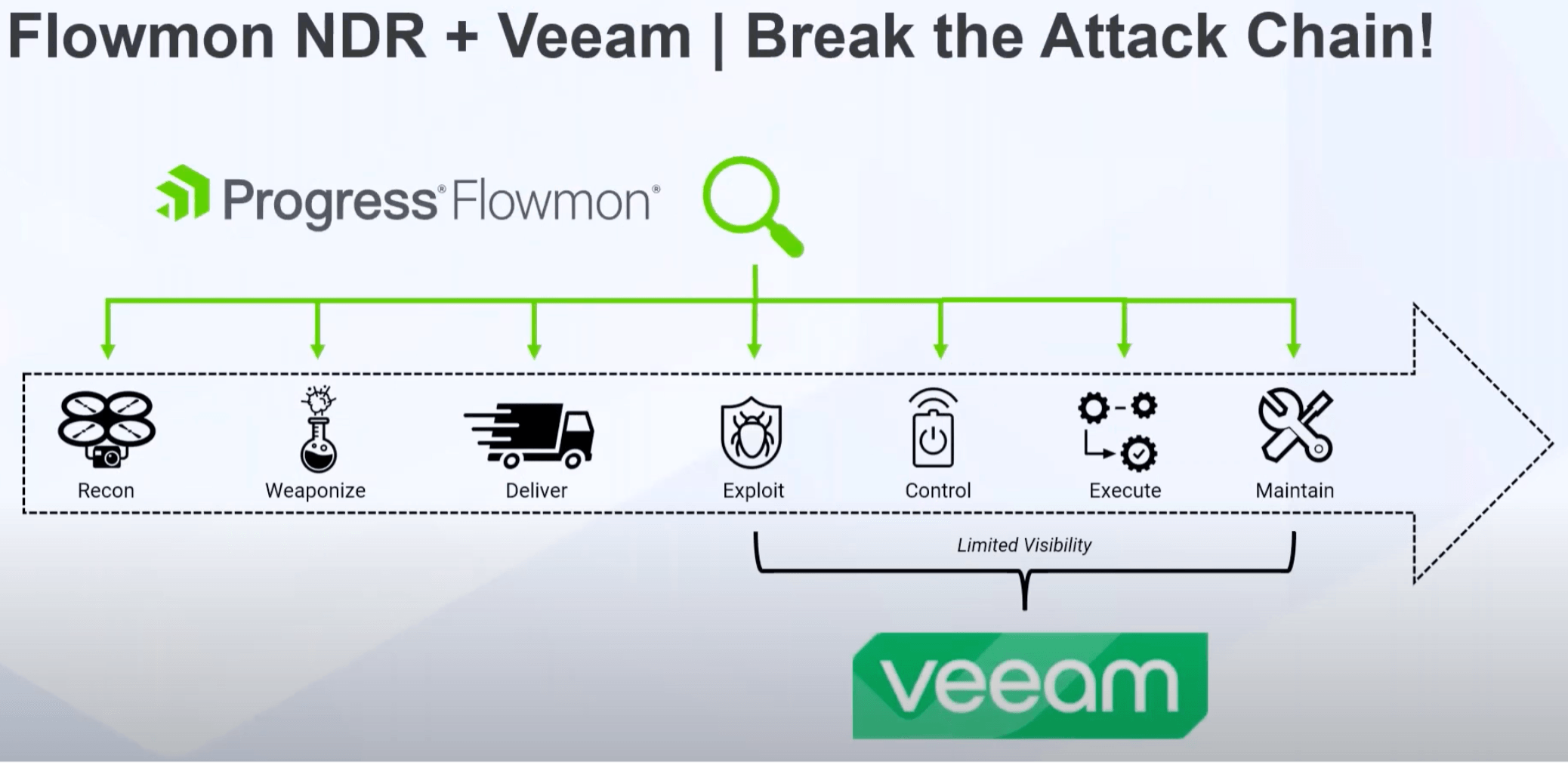
Figure 1: The Cyber Attack Chain and where Flowmon and Veeam can break it
Understanding the cyber kill chain is crucial for effective defense, and the combination of Flowmon and Veeam creates a toolset capable of disrupting many stages of an attack. Flowmon early threat detection solutions, combined with Veeam’s robust data protection and recovery capabilities, create a thorough defense that spans the entire attack lifecycle.
Flowmon excels in the early stages of the attack chain, leveraging its advanced Anomaly Detection System (ADS) to identify potential threats before they can gain a foothold. Its AI-powered analysis of network traffic can spot subtle anomalies that might escape traditional security tools. The smart prioritization capabilities of Flowmon enable security teams to focus on the most critical alerts by cutting through the noise and focus on what is most important.
Flowmon automated analytics continuously monitor network behavior, detecting even the slightest changes that could indicate an attack is in progress. Underpinning all of this is the built-in experience engine, which provides in-depth and valuable information about threats. The engine leverages well known frameworks like MITRE ATT&CK, along with heuristics and machine learning, to provide in-depth threat detection that delivers information to security teams in understandable and actionable ways.
Veeam complements Flowmon by providing industry-leading backup and recovery across on-premises, cloud and hybrid environments. Its flexible deployment options support virtual machines, containers and physical and SaaS deployments, helping protect an organization’s data regardless of location.
Veeam’s Recovery Orchestration feature automates disaster recovery planning and testing so that organizations can quickly bounce back from an incident. The Veeam Backup and Recovery solution provides data availability across various platforms, while Veeam Monitoring and Analytics offers crucial insights into the backup infrastructure and potential issues.
One of Veeam’s key strengths is its native APIs, which enable more seamless communication with Flowmon. When Flowmon detects a threat, it can immediately alert Veeam, providing detailed information, including timestamps, IP addresses and hostnames of affected systems. Veeam then marks potentially compromised backups, and subsequent backups are also flagged until any issues get resolved.
This integration gives backup administrators unprecedented visibility into potential infections, allowing for prompt action to secure systems and data. By combining Flowmon network threat detection with Veeam’s data protection capabilities, organizations can significantly reduce the time between detection and response, minimizing the impact of potential breaches.
The Veeam Data Platform (VDP) enhances this integrated approach with its Respond and Recover feature, which helps organizations rapidly recover from ransomware and other attacks. By providing immutable backups, orchestrated recovery processes and granular recovery options, VDP allows organizations to restore their data and systems quickly and efficiently.
Moreover, Veeam’s Secure and Compliant feature means that data remains protected and in compliance with relevant regulations. With robust encryption, access controls and in-depth audit logging, organizations can feel more confident about the security of their data at rest and in transit. The Veeam Detect and Identify capability scans backups for potential malware or anomalies and provides visibility into backup integrity.
Flowmon and Veeam ADS Integration
The integration of Flowmon ADS with Veeam’s platform takes threat detection and response to the next level. Flowmon ADS continuously monitors network traffic, identifying potential threats in real time. When a threat is detected, Flowmon can trigger Veeam’s incident API which then alerts backup administrators to potential compromises in their backups. This collaboration enables security and backup teams to work together, mitigate threats and recover data rapidly.
Try Flowmon for Yourself
Visit the Flowmon platform page for details on Flowmon and the Flowmon ADS page for information on ADS. To connect with a product specialist about how Flowmon can help improve the security of your networks, contact us.
For a demo of Flowmon to see how it can deliver actionable insights for your organization within minutes, visit our Flowmon Guided Demo page.
Filip Cerny
Product Marketing Manager

Latest Stories in Your Inbox
Subscribe to get all the news, info and tutorials you need to build better business apps and sites