Key Fortinet and Flowmon Integrations: Automated Incident Detection and Response

Flowmon has recently joined Fortinet’s Open Fabric Ecosystem by integrating with FortiGate and FortiSIEM. This cooperation brings automated system for threat detection and response, blocking security risks in their infancy, and giving time to administrators to carry out forensics.
Threat actors constantly modify code and use advanced techniques to avoid detection, but they still leave footprints scattered all over the network. Flowmon monitors east-west traffic to identify threats in their early stages by using a technology called network behavior anomaly detection (or network traffic analysis). Using a plethora of methods based on machine learning, heuristics, adaptive baselining, signature-based detection, threat intelligence, and more, it is effective at every stage of an attack, from reconnaissance to data exfiltration.This is very useful for uncovering malware in general, phishing, targeted attacks, or risky assets breaching compliance policies, even in encrypted traffic. Let’s demonstrate the mechanics of the integrated Fortinet-Flowmon solution by the scenario of responding to malware activity in the network.
Malware Detection and Automated Blocking
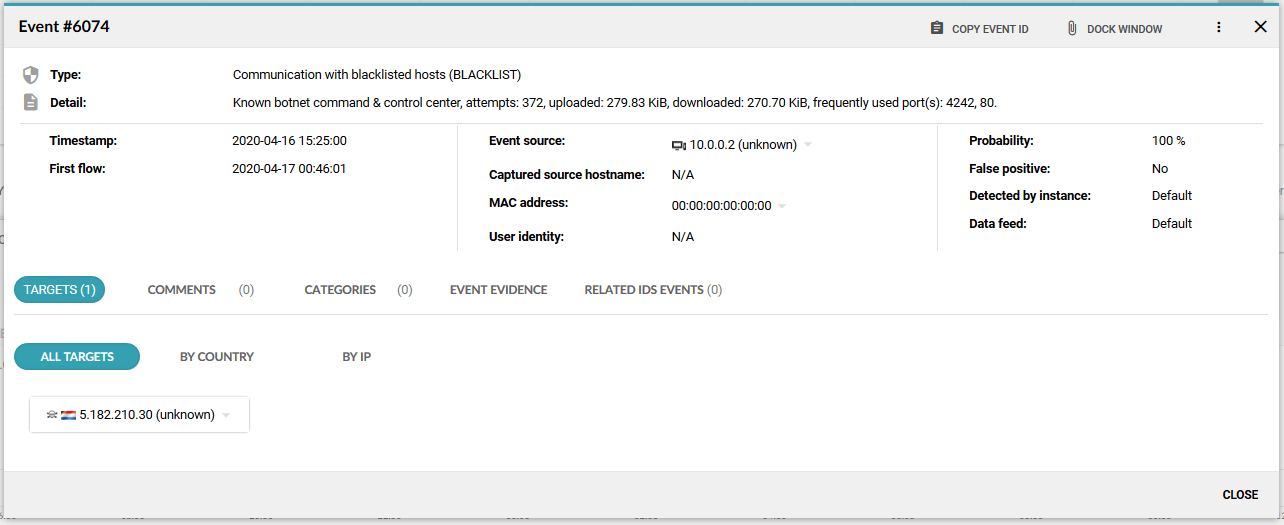
There is a malware-infected laptop in the network. The initial intrusion was performed when the laptop was connected from home, and there was no perimeter security to prevent this. Once the laptop is back in the corporate network, it communicates with the botnet command & control center to get instructions on further activity. This is detected by Flowmon using the Threat Intelligence approach.
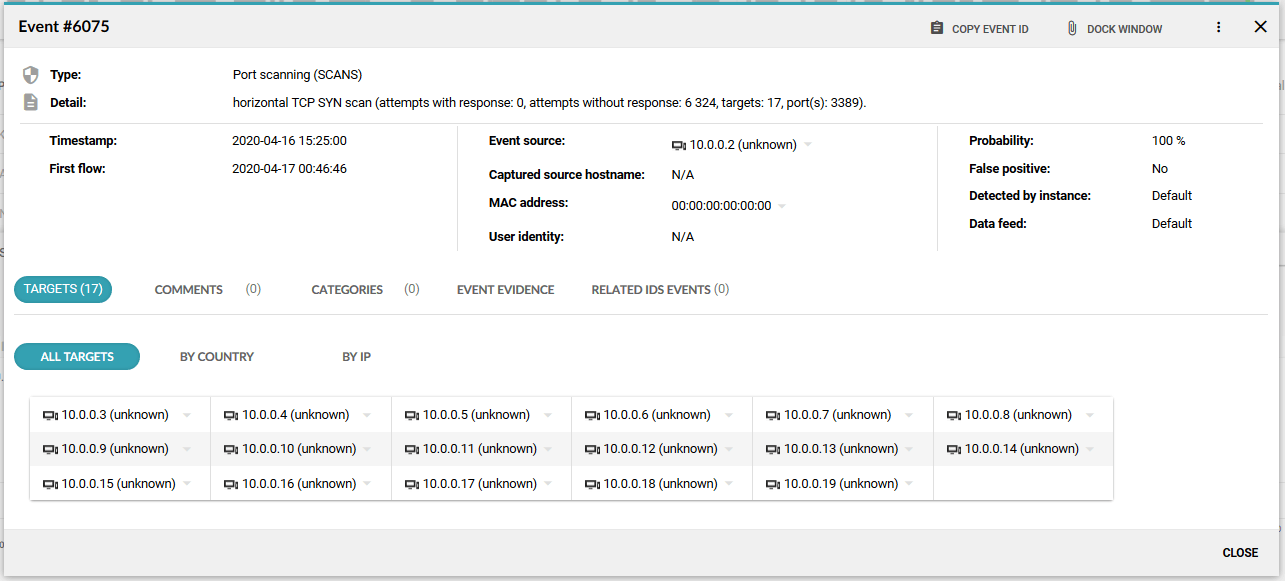
After receiving instruction from the C&C center, the laptop starts scanning the network in order to identify potential victims to spread to.
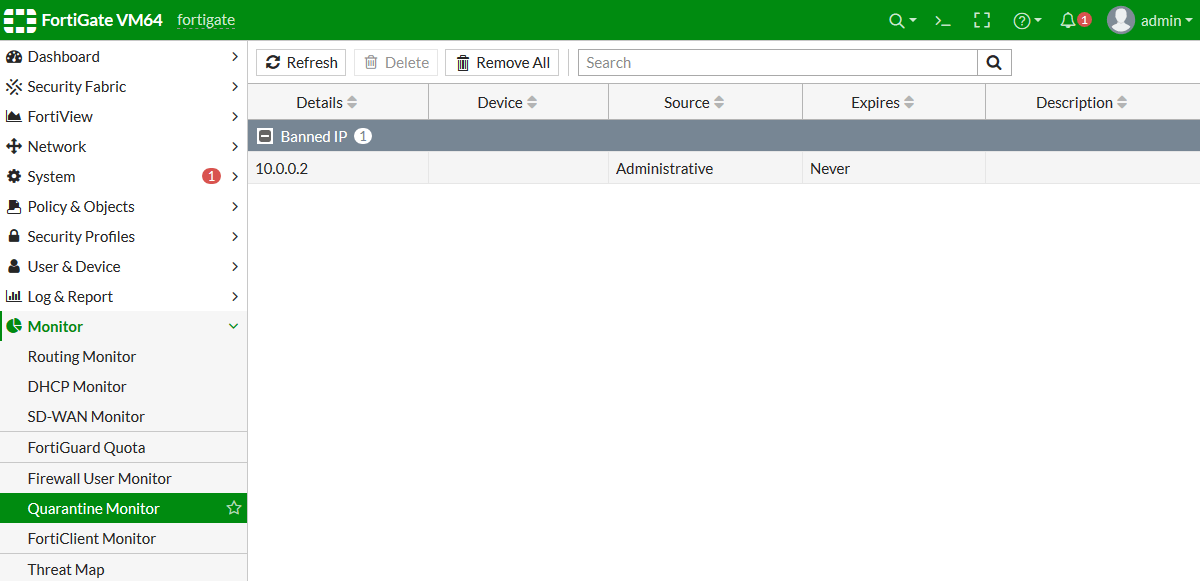
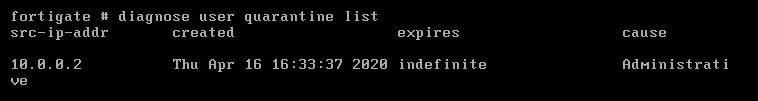
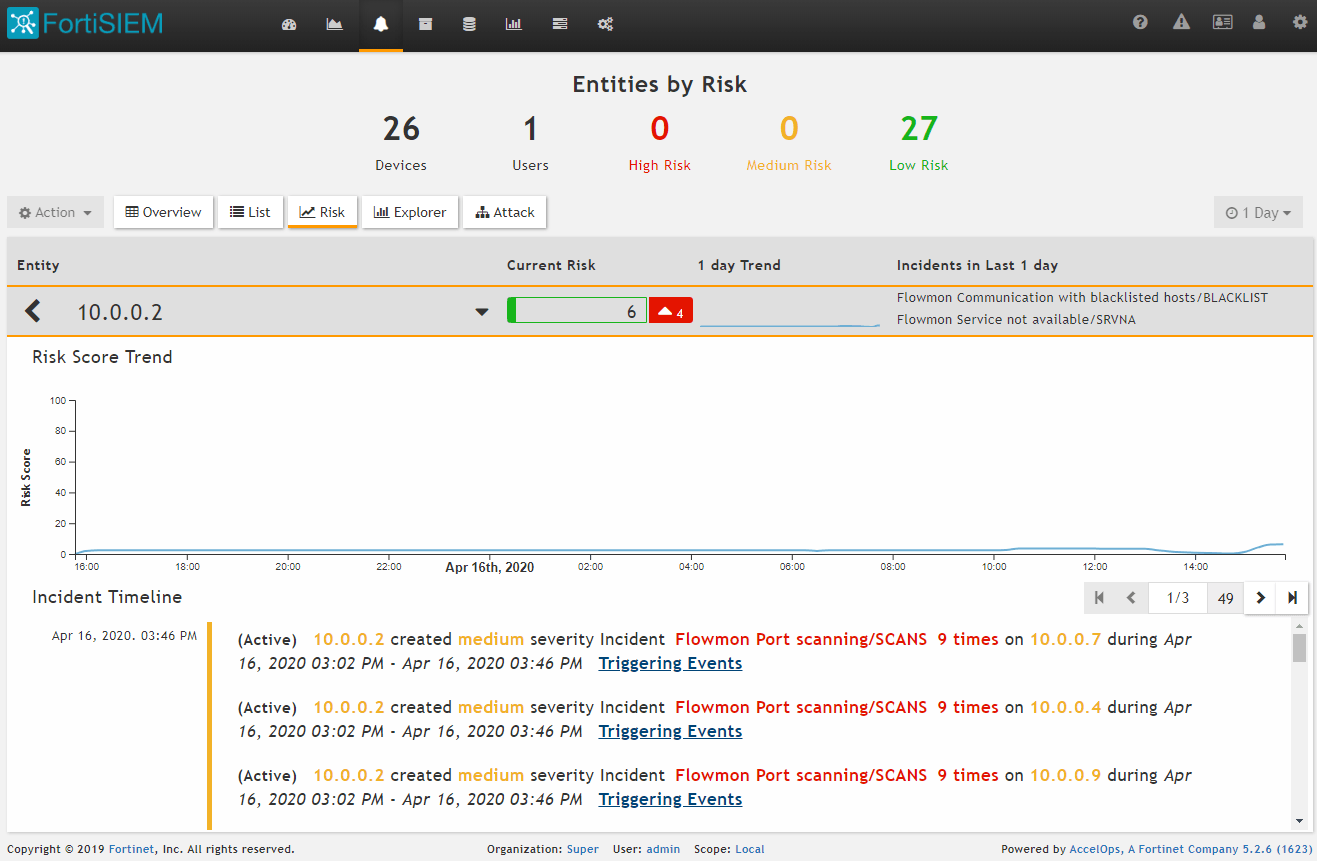
Before any infiltration attempt was successful, Flowmon had connected to FortiGate and provided instruction to quarantine the infected laptop with IP address 10.0.0.2. The new rule was successfully implemented, as we can see in the FortiGate Quarantine Monitor. This action blocks the network activity on the perimeter (north-south) where the FortiGate firewall is located and does not stop the potential spread of infection on the local network (east-west). Blocking the north-south traffic cuts off the communication with the botnet command & control center or attacker remote access channel and prevents data exfiltration or additional download of malicious content. This action prevents the most severe damage and creates reasonable conditions for the security team to contain the threat.
Security analysts can now investigate the incident. In Flowmon, we have quickly filtered a list of all events related to this IP address.
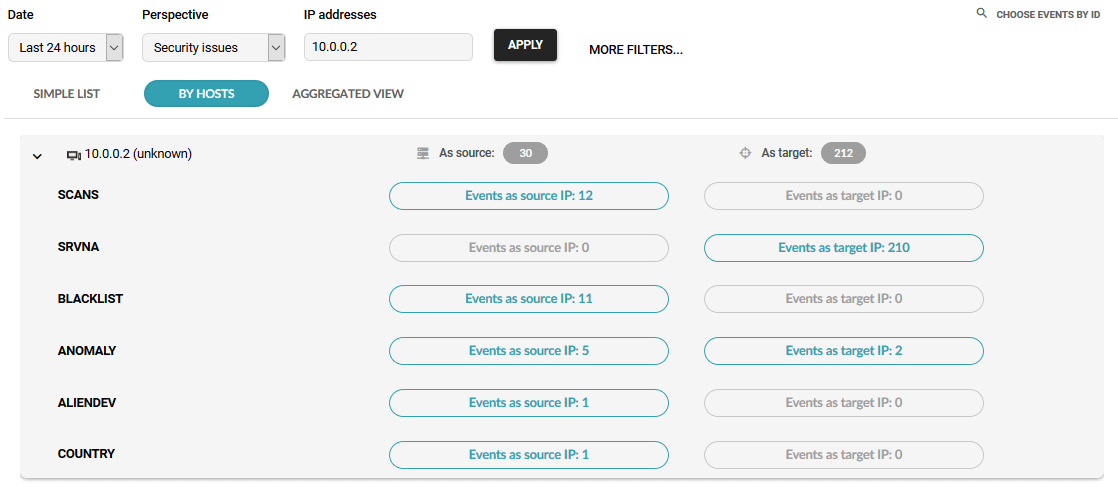
There is a built-in analytical workflow to investigate the incident further, including the timeline of events, all related indicators of compromise, communication partners from event explanation level all the way to packet data stored automatically for post-compromise forensics.
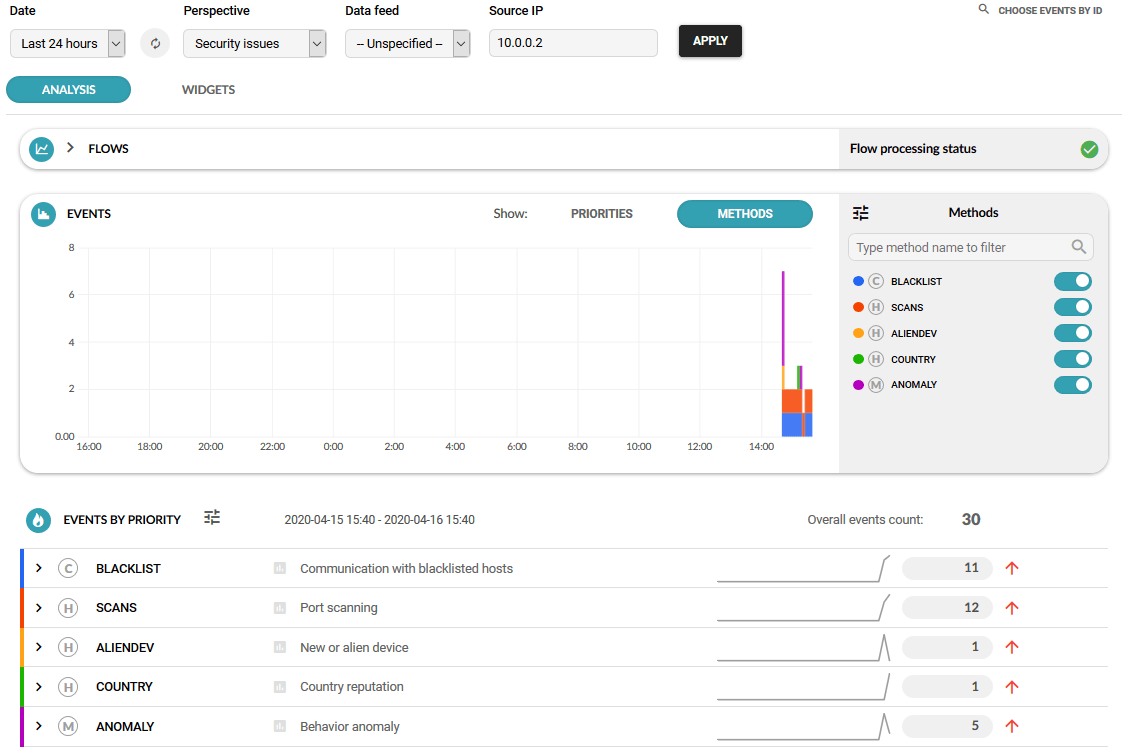
Flowmon automatically logs all the related events to FortiSIEM. Configuration requires a few steps but doesn’t take longer than 30 minutes.
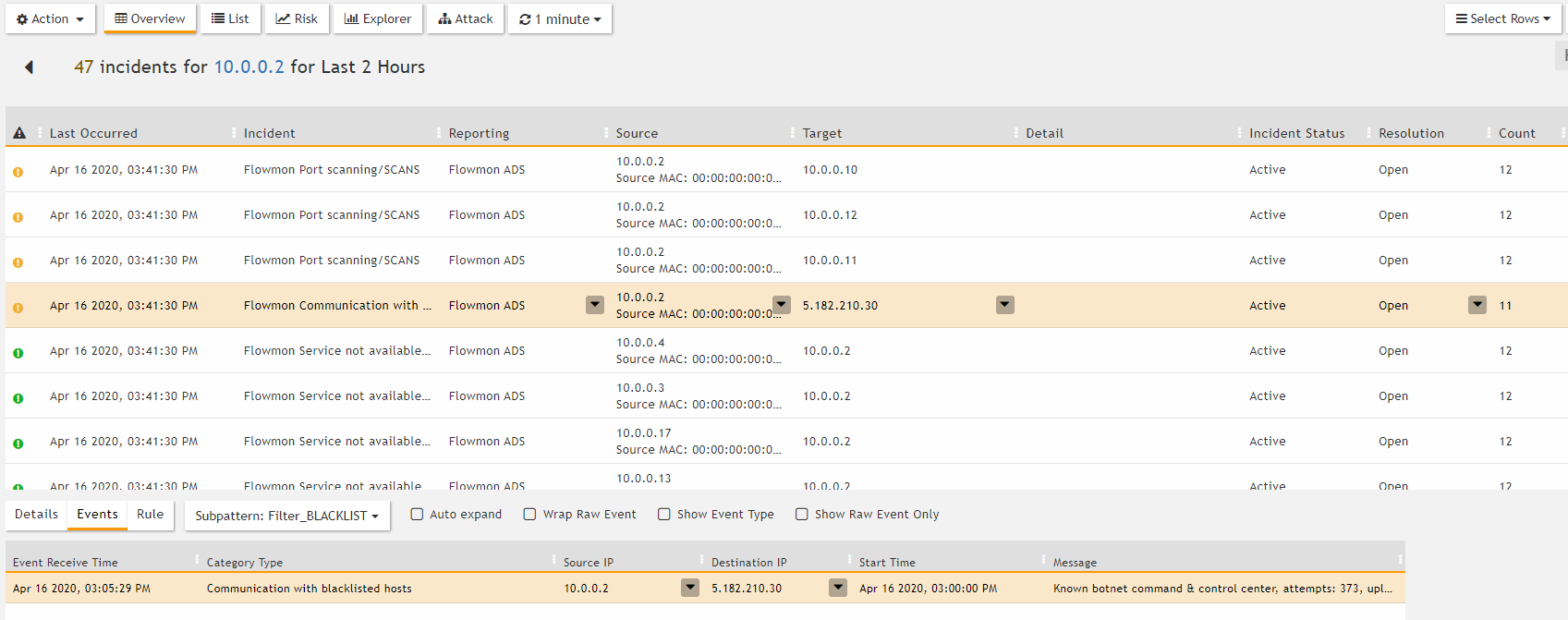
FortiSIEM collects events from Flowmon using Syslog in CEF format and further sorts, correlates, and reports on them. In the example below, we see an overview of incidents created for one single entity (IP address).
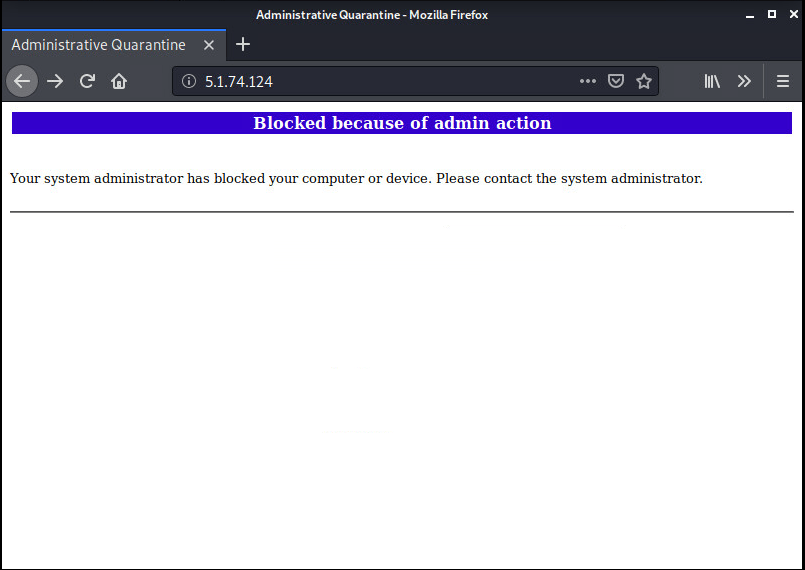
When the user accesses the internet, their access is blocked, and FortiGate shows a message that the device was blocked by the administrator.
Multilayered Security
There are certainly many different ways how to configure Fortinet and Flowmon to work together. But the goal is always the same: to create a highly automated security system that helps administrators to protect their assets from both external and internal threats.
When FortiGate watches the perimeter and protects against external threats, Flowmon analyzes traffic in the network to detect unknown and insider threats that originate from within. Once Flowmon detects a sign of a threat (e.g., reconnaissance or lateral movement of an attacker), it sends a message to FortiGate, which in turn blocks the communication on the perimeter.Simultaneous deployment of several detection techniques allows uncovering a wide spectrum of threats and makes life much easier for security administrators. What more, threats remain blocked for weeks, creating plenty of time for investigation and remediation.
Further resources
- Flowmon - FortiGate integration package, as well as Flowmon - FortiSIEM integration package can be found on Flowmon Portal. For more information, contact us at support@flowmon.com
- If you want to know more, watch this webinar on Flowmon YouTube channel
- Joint solution whitepaper
