How to enable signature-based detection in Flowmon Probe and Flowmon ADS

Leveraging signature based detection with NDR tools brings many benefits. Lets have a look how you can enable Suricata IDS on Flowmon solution.
In this article, we explained the benefits of combining signature-based detection by Suricata IDS with behavior-based detection by Flowmon ADS. Now, let’s talk about how to enable this feature using Flowmon Probe and Flowmon ADS.
Suricata IDS requires access to traffic to analyze packets and look for known patterns. To do its work, Flowmon Probe requires access to network traffic as well. It just makes sense to have the Suricata installed and running on the Flowmon Probe. For this purpose, we offer Flowmon IDS Probe module that installs Suricata on Flowmon Probe to save you time and effort by deploying standalone Suricata. Flowmon IDS Probe package is available on support portal and it installs Suricata IDS to the Flowmon platform with community rules. This package is provided free of charge and does not require to have any special license. However, the Flowmon IDS Probe is not covered by Flowmon support service.
After you install IDS Probe module on your Flowmon Probes, there are a couple of simple configuration steps you need to do to get the IDS events to the Flowmon ADS. If you are running ADS on a stand-alone probe, you can skip the first two steps.
IDS Probe module configuration
STEP 1:
Configure Syslog Event Logging on all probes with the IDS Probe. This will ensure that the IDS events are exported via syslog to the target collector with Flowmon ADS. You can do so in the Configuration Center > Settings > System Settings > Syslog Event Logging. Here you need to enable the syslog event logging and add a new server. Then just enter the IP address of the collector with ADS and specify the port and protocol. Don’t forget to save the settings.
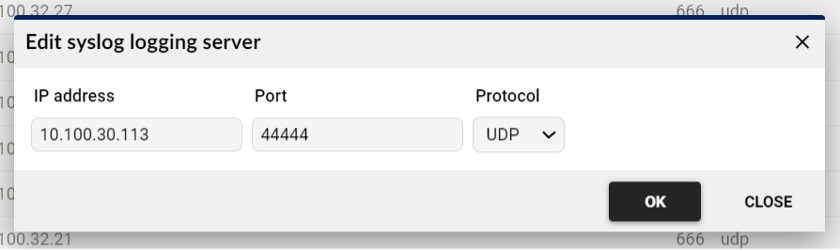
STEP 2:
On the collector side, we need to configure Syslog Server. Navigate to Configuration Center > Settings > System Settings > Syslog Server. Enable external syslog and add new syslog client. Enter the IP address of the Flowmon Probe, use the same port and protocol and save.
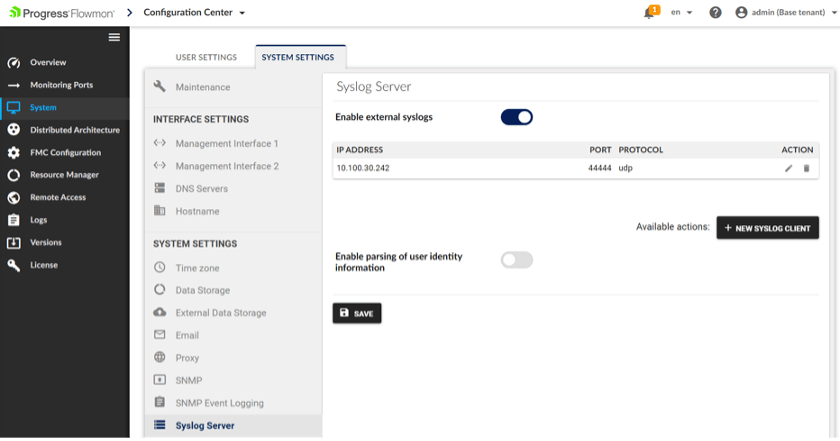
STEP 3:
Now the probe is sending IDS events via syslog and collector is receiving it, but to process, store and visualize it, we just need to do one more thing. Go to the ADS Settings and in the System Settings > IDS Collector click on ‘Activate’ button. After this is done, you will be able to see IDS events on the Analysis page.
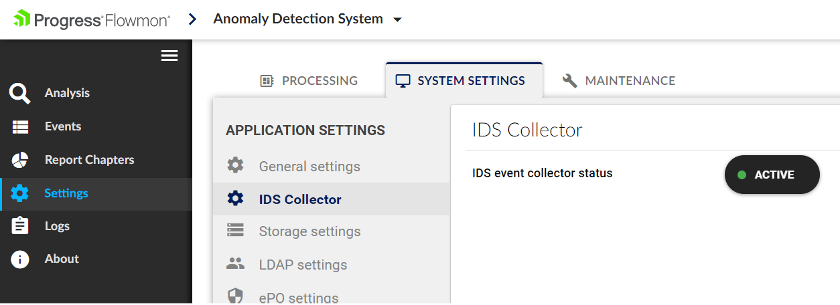
There are also more nuances to running the Suricata IDS, but for this purpose, we have a user guide on configuration and tuning. It is available on our support portal as well. Follow the guide to learn how you can tune the false positives, manage the detection rules, set up network variables, or create your own categories, etc.
This is how simply you can enable the signature-based detection on the Flowmon ADS. You just need Flowmon Probe and of course, the ADS module. If you are already running Suricata IDS on some other server, you can do the same, just configure it to export the IDS events via syslog to the Flowmon Collector and repeat steps 2 and 3.
