Nail These 6 Encrypted Traffic Cases with Flowmon

There is no doubt SSL/TLS offers major benefits, such as confidentiality and integrity. However, it also creates challenges. For instance, visibility gaps and management overheads. Furthermore, malicious threats are evolving and adopting encryption to cover their tracks. In this article, we'll look at how Flowmon can help tackle some of these challenges.
In January 2016, Michael S. Rogers, the director of the National Security Agency, said: "Encryption is foundational to the future". And with the ever-increasing amount of internet traffic encrypted it looks as though the future is finally here. It only took slightly under 3 years. You can read more about the rise of encrypted traffic in our previous post Can Flow Monitoring Work on Encrypted Traffic?.
We've added support for Transport Layer Security (TLS) to Flowmon to help you with encrypted traffic use-cases. We can loosely divide them into two categories. The first being cryptographic assessment. We investigate SSL/TLS protocol versions, cybersuites (encryption algorithms, key lengths) as well as certificates. The second category is monitoring and security. Here, we can leverage JA3 fingerprinting to pinpoint suspicious actors, use Application-Layer Protocol Negotiation (ALPN) to identify protocols in encrypted communication, investigate Server Name Indication (SNI) and much more.
Let's look at some TLS use-cases.
Cryptographic Compliance
Cryptographic assessment or compliance is when we audit our encryption stack to look for outdated protocols still in use, inadequate key lengths and expired certificates.
Use Case 1: TLS protocol version
Currently, there are several versions of TLS:
TLS version 1.0 was released way back in 1999 (as a successor to SSL). This almost 20-year-old protocol is vulnerable to various attacks (such as POODLE), uses weak cryptography and is no longer compliant with the Payment Card Industry Data Security Standard (read Flowmon for PCI-DSS compliance).TLS 1.1, think Windows 8 of TLS, rarely used, superseded by a newer version. There is no point in using TLS 1.1 when you can use TLS 1.2.
Apple, Google, Microsoft and Mozilla are all planning to deprecate both outdated versions in 2020. GitHub already disabled support for both in February. On April 1st, DigiCert disabled TLS 1.0 and 1.1 for all their services. Cloudflare dropped support for both in June.
Figure: Protocol Support (Source: Qualys SSL Labs - SSL Pulse, November 2018, CC BY 3.0 US)
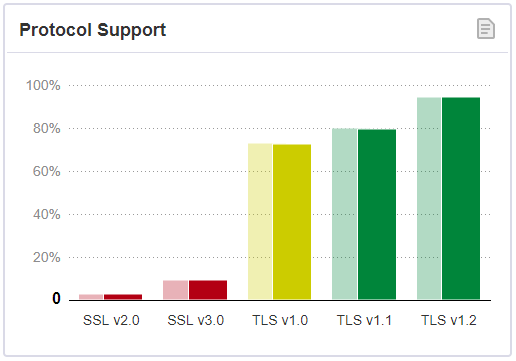
TLS version 1.2 was released in 2008 and it's the most used version today. The upcoming TLS 1.3 improves security by dropping outdated and vulnerable algorithms (RC4, SHA-1) and also improves the speed with a faster initial handshake and 0-RTT Resumption feature.Which TLS versions are out there in the wild? SSL Pulse provides an excellent dashboard updated every month with statistics about SSL/TLS versions, key lengths, cybersuites and vulnerabilities. You can check the SSL/TLS version of your browser with How's My SSL?.
With Flowmon it's easy to inspect the use of outdated TLS versions in your network. Take a look at this screenshot from Flowmon Monitoring Center:
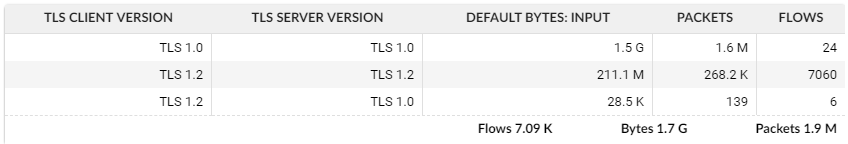
Looks like there is a lot of traffic still using TLS 1.0. We can dig deeper and find out which local services / applications need to be upgraded:
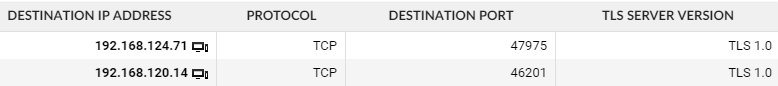
Use Case 2: Public key length and algorithm
Weak short keys and outdated algorithms are a serious security risk. Insufficient key length makes it easier for an attacker to perform brute force decryption. Outdated algorithms suffer from vulnerabilities malicious actors can exploit to break in (think Heartbleed). We should always check the key length and algorithm as one because different algorithms require different key lengths, for example, elliptic curve cryptography algorithms (ECC) have shorter keys while having equivalent key strength as RSA (RFC 4492):
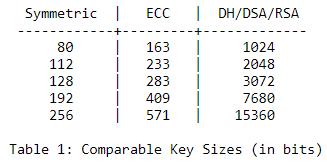
Let's inspect public key lengths and algorithms in our network with Flowmon:
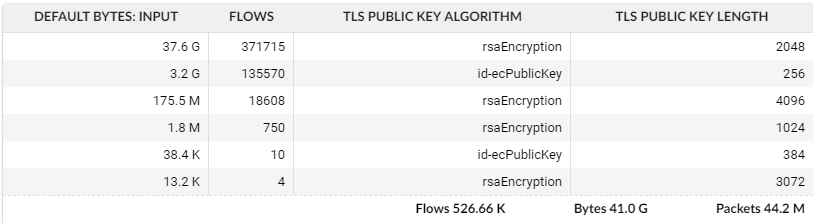
The values in TLS PUBLIC KEY ALGORITHM column are straight from RFC 3279. The value rsaEncryption stands for RSA public keys and id-ecPublicKey represents two elliptic curve algorithms: ECDSA (Elliptic Curve Digital Signature Algorithm) and ECDH (Elliptic curve Diffie–Hellman).
As we can see most of the encrypted traffic is using RSA with 2048-bit length, followed by ECC with 256-bit length (which is a rough equivalent to RSA 2048-bit) and followed by RSA with 4096-bit keys. This is good news, since it's recommended to use 2048-bit keys for RSA (Qualys Grading). However, there is still a small amount of traffic with only 1024-bit RSA keys. We can use filters to focus only on this traffic:
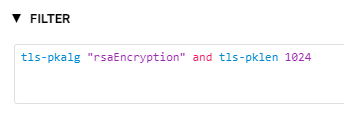
Here is the snippet of output:
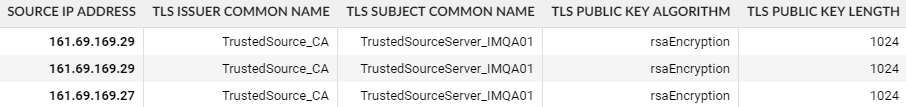
We could find the usage of short TLS keys in our network and we can take action to set it right.
Flowmon enables you to set an alert any time a weak key is detected in your network:
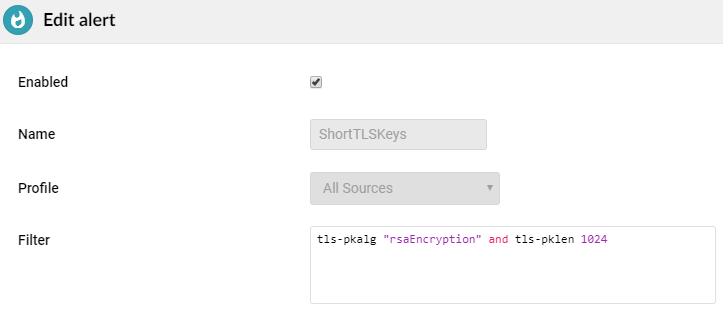
...and optionally send an email:
Use Case 3: Certificate checkup
While checking for expired certificates is an obvious step, we might also want to check for soon-to-be-expired certificates to prepare in advance. Furthermore, monitoring certificates and their usage in development, testing and production environments is a way to protect against and identify leaking private keys and other sensitive information.
Example of the expired certificate (notice the value in the last column):
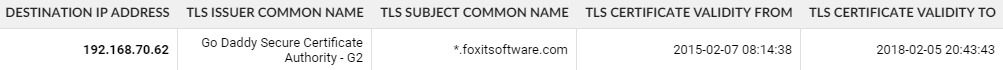
We can look for certificates that will expire between today and by the end of the year using this filter:
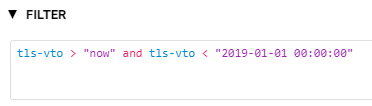
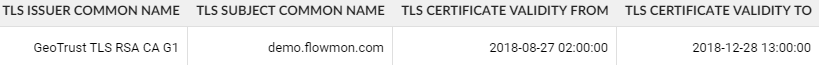
This is a great tool for inspecting your own services. For example, it looks like the certificate for our public demo will expire near the end of December, so we have to make sure we take action before then:
Security and Monitoring
Malicious threats are increasing the adoption of SSL/TLS. Deepen Desai, senior director at Zscaler, reported the number of phishing attempts delivered over SSL/TLS has increased 400 percent since 2016. According to Gartner, by 2019, more than 50% of new malware campaigns will use various forms of encryption and obfuscation to conceal delivery and ongoing communications, including data exfiltration. Encrypted traffic will carry over 70% of web malware by 2020. In the most recent Cisco Annual Cybersecurity Report, the amount of malware encrypted network communication increased more than 3 times over a 12-month period. So it's clear we need an encryption resistant tool to help us fight the baddies.
Use Case 4: JA3 Fingerprinting
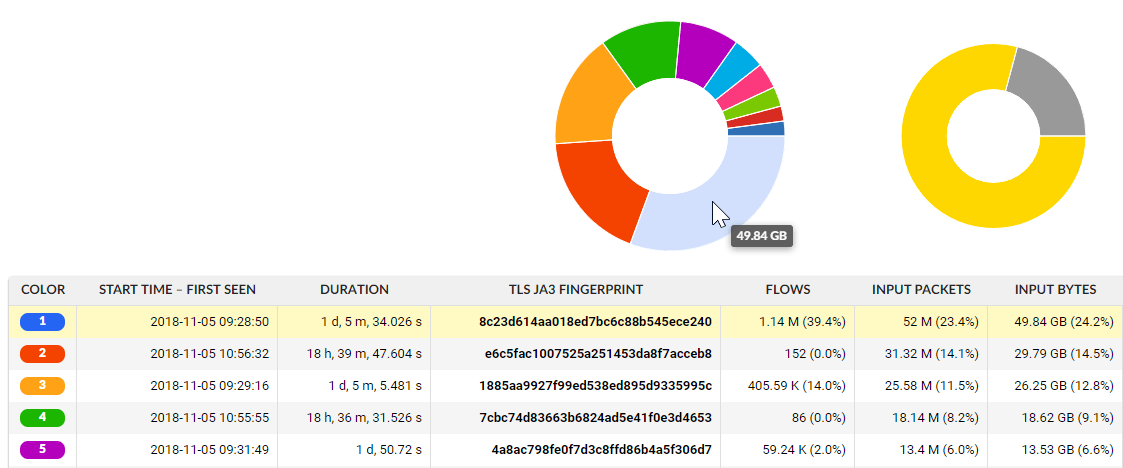
One of the easiest way to spot malicious threats or at least to provide an indicator of compromise (IoC) is JA3 fingerprinting, named after its three authors with identical initials "J.A.". This experimental method combines these five parameters of TLS communication: version, ciphers, extensions, elliptic curves and its formats and produces a MD5 hash. This is our JA3 fingerprint. Interestingly, this is enough to identify various clients. For example, "e7d705a3286e19ea42f587b344ee6865" is the JA3 fingerprint for a standard TOR client. The reasoning behind this method is the idea that tools are more difficult to change than IP addresses or domain names. This method is very much in the field of signatures, and as such is highly reliant on available blacklists and whitelists. Nevertheless, you can leverage it to find outliers and other oddities in your network.
Use Case 5: Protocol identification with ALPN
Application-Layer Protocol Negotiation (ALPN) is a TLS extension. With it, we can identify L7 layer protocols inside encrypted traffic. Supported protocols are several versions of HTTP, SPDY, NAT, WebRTC, FTP, IMAP, CoAP and other experimental protocols.
Use Case 6: Server Name Indication (SNI)
Similarly to ALPN, SNI is a TLS extension. It allows TLS-capable servers to host multiple services on the same IPs. Clients add this extension with the hostname of the website they want to connect to.
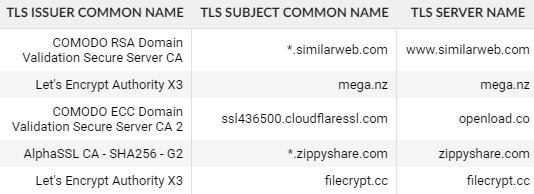
Looks like one of our employees was violating company policy by visiting file sharing websites:
Summary
Companies risk serious consequences when ignoring encrypted traffic. Malware campaigns are increasingly taking advantage of encryption to hide. Flowmon enables regular cryptographic assessment to check for compliance with the latest security standards. Review the validity of certificates, pinpoint suspicious clients and much more, all without the need to breach user privacy with Flowmon 10. Set alerts to notify you whenever TLS parameters violate your internal policy.And how will you leverage the new TLS capabilities?
Roman Luks

Latest Stories in Your Inbox
Subscribe to get all the news, info and tutorials you need to build better business apps and sites