Hunting Frequent and Dangerous #1: Protection against Pharming, Phishing and Botnets

In our previous article we discovered the most common types of cyberattacks. We also learned how they are designed and how they operate. Such understanding helps us build adequate and effective protection strategies.
#1 Pharming: a Black Widow Spider’s web
When you type google.com into your web browser, it will ask a Domain Name Server to translate the domain address to an IP. To speed this process up, commonly accessed domains and their respective IP’s are stored in a local file called Hosts. Attackers usually target the modification of these files and use different types of malware to do so.
From the user’s perspective, redirection by a compromised DNS server can only be detected using advanced behavior analysis and machine learning. Ultimately in combination with the most precise way to protect against Pharming - the Threat Intelligence approach - where communication is shared about malicious pages by using a blacklist of known threats. Threat Intelligence is effective for both types of redirection, Host file modification, and DNS misuse.
#2 Botnet: Hitchcock’s Birds
Different approaches to detect botnet behavior were used over the past decade when armies of compromised machines became popular. Such approaches often counted on the fact that a compromised station - part of a botnet - regularly communicated to their command and control server (C&C). However, the real situation also showed many other applications and services presenting the same sort of behavior and thus such a technique brought an unbearable amount of false positives. Detecting C&C server communication with perimeter security isn’t the solution to reach out for as many still think. Firewalls, including the next generation ones, rarely consider outgoing communications whatsoever and are therefore blind. Again, Threat Intelligence plays a big role in identifying Botnets. In databases of known botnet command and control servers you’ll find their IP addresses. But, as IP’s of C&C servers change all the time we should try to be more precise.
There are more advanced databases that work with C&C server domain names such as one of the Gameover ZeuS’s C&C server on the domain “31pot27uv8ay1fncg8twe7212.com”. The solution? To guarantee a high level of security, monitoring all HTTP communication and alerting on communication with such domains must be considered. But not every vendor that can monitor HTTP traffic complies. It is crucial to have a scalable solution that can identify the bad guys on high network speeds, a solution that provides close to real-time detection capabilities as possible, with complete and deep evidence data for post-compromise analytics.
Now what happens if the C&C server no longer responds to its domain? HTTP communication monitoring and alerting becomes worthless. It still means your stations are compromised even if no connection is established to the C&C server. When contacting such an unusual domain for the first time, it needs to be translated by DNS. If the DNS communication is monitored, an attempt to connect to a malicious domain can be picked up. Again, as perimeter security rarely monitors outgoing communication, internal network monitoring with automated detection is the way to go. This approach can be applied to all the types of attacks I have talked about in this article.
#3 Spear Phishing: Sirens luring sailors into a trap
Protection strategies fighting Spear Fishing are very similar to those for Pharming. A common way to make users access a malicious website and give away their business sensitive information or financial credentials is by asking them in an email. Mail filtering is the first step that can block malicious emails. Preventing a dangerous email to get through to the user is very important, although reality shows no vendor can guarantee 100% reliability. Second tier protection with early detection and impact analysis is absolutely essential. So, after the phishing email passes through the mail filtering algorithm, we need to ensure that the detection capabilities will protect us against connecting to a malicious website.
One of the most broadly used databases of phishing pages is PhishTank.com. According to their stats, they have 2,074,066 ‘Phishes’ reported up to date. Only 33,210 of those are online and accessible, and the rest of over 2M of them are not.
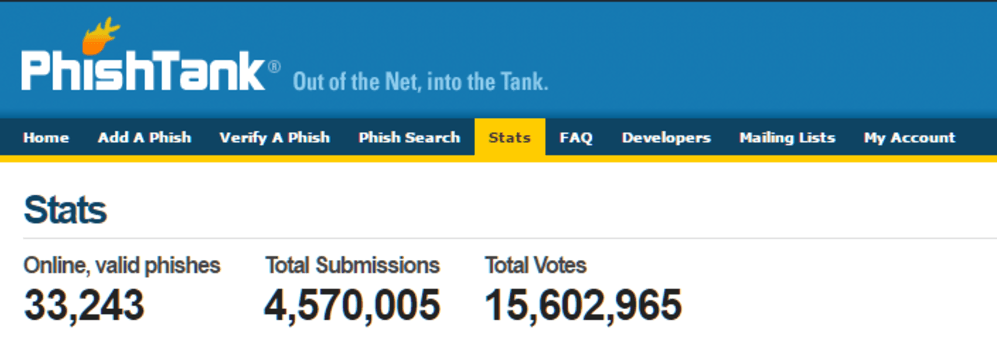
Threat Intelligence is still a new and emerging technology and when applied in a multilayer and mature way as described above, it can become a very precise detection method to alert you to a whole range of attacks. Sometimes the simplest and most straightforward way is the most efficient one.

Latest Stories in Your Inbox
Subscribe to get all the news, info and tutorials you need to build better business apps and sites