Resource Misuse Detection with Flowmon ADS

An example on how flowmon helps to detect unwanted software running on your network.
In this post, we present a short example on how to notice even the most subtle hints your Flowmon Anomaly Detection System gives you. We show why it is good practice to use Anomaly Detection in the first place – as we will certainly discover something our firewalls, IPS systems or endpoint security did not.
1. An example
Take a look at the traffic shown in the figure below. Without jumping to conclusions, everything appears normal and unsuspicious… Yet, the Flowmon Anomaly Detection system displays small spikes. Let us investigate a bit more.
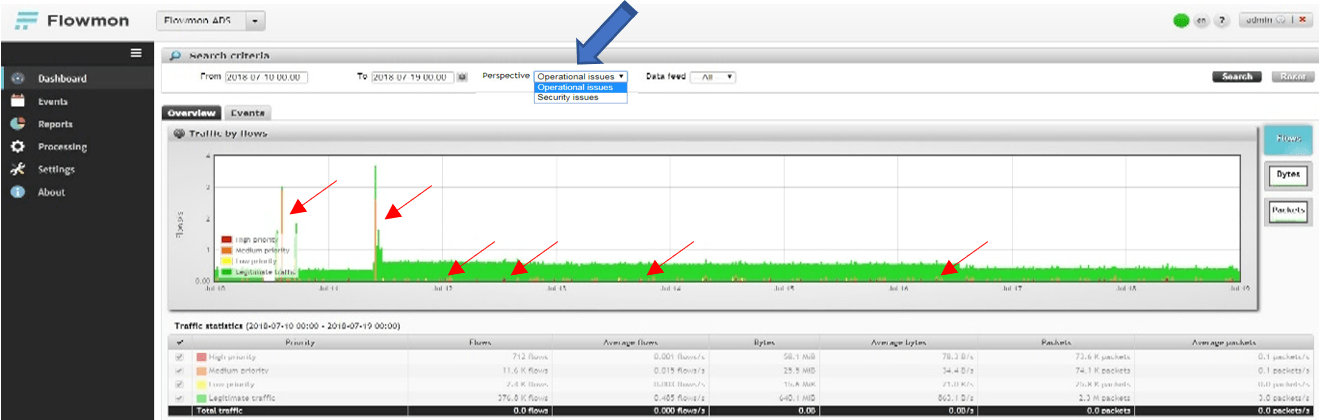
1.1 What the hints are
We see
- we are communicating with countries that are known to have low reputations
- devices that have just appeared on our network
- devices that exhibit anomalous behavior or more diverse communication than usual
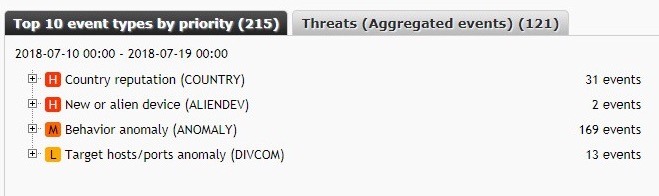
Opening the lists, there is one host that stands out:
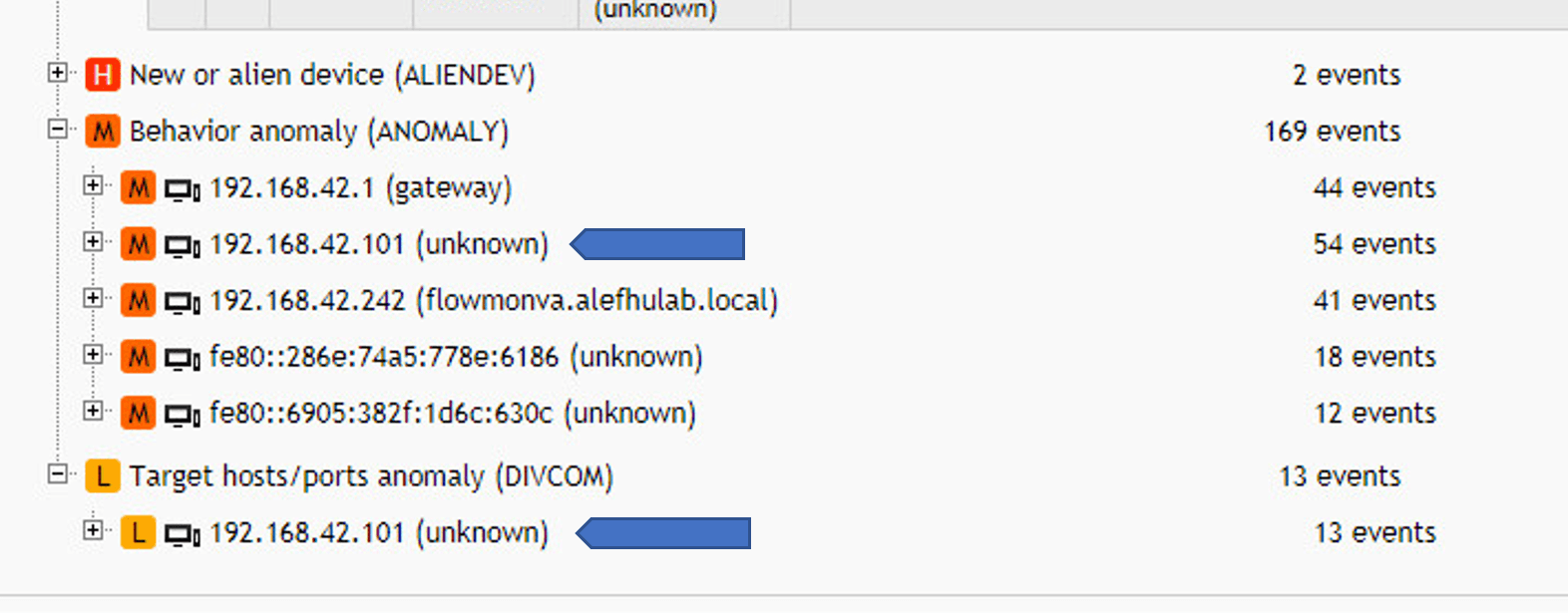
1.2 Investigation
Let us investigate further and look into event evidence – a view with more details.
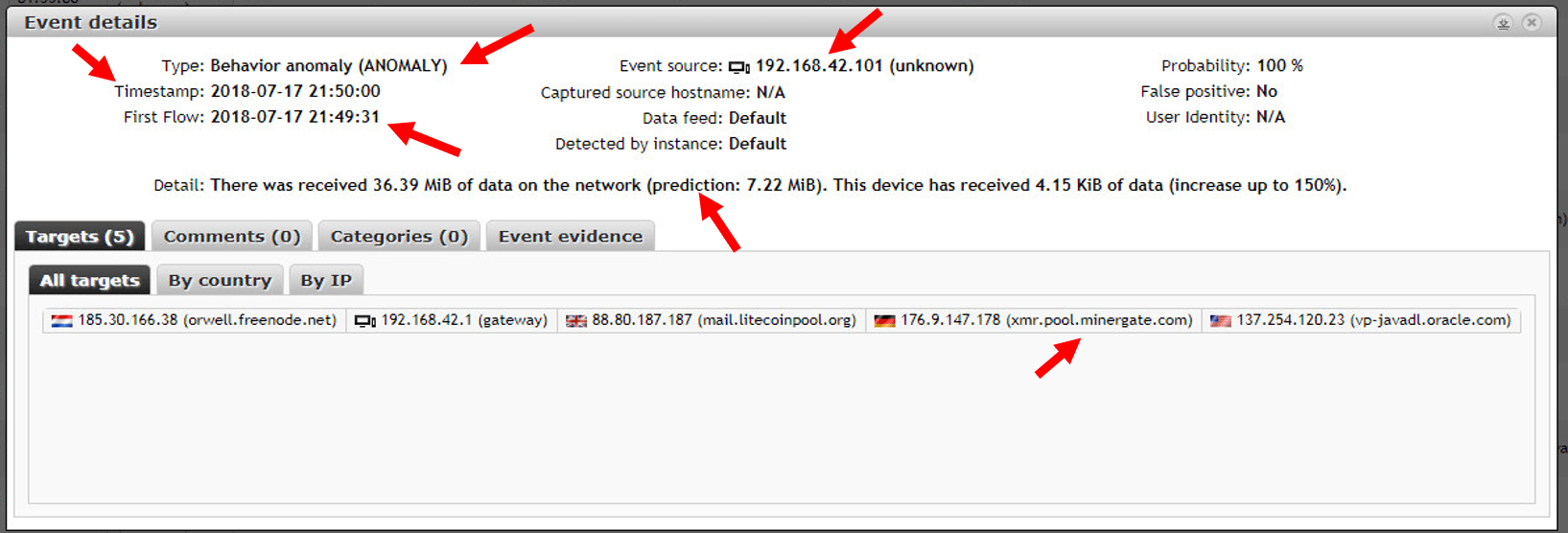
We can now recognize that our host in question had somewhat more traffic than expected. The FQDN xmr.pool.minergate.com gives us even more hints on what is going on…

1.3 The host in question
So what has happened?
We need to look at the host to discover it is running a very smartly engineered application that mines cryptocurrency. It runs very slowly with obtaining the hashes, has valid signatures – no endpoint security software or network IPS alerted us about the activity.
2. Key takeaways and conclusions
We hope our short example proved our point: resource-misusing software can be advanced enough to pass existing, signature-based defenses. However, there will always be small hints (we like to call them anomalies) that we can follow - even before systems that know exactly what to look for.
Anomaly detection paired with strong analytics capabilities (i.e. the ability to look at who is talking to whom as soon as we get hints of unwanted behavior) provides another layer of security against rapidly evolving threats. Detection of this specific crypto-mining software has been added to the set of Behavior Patterns and distributed to our customers. Now customers will be notified via the BPATTERNS detection method that hosts are running this exact malicious software. However, it is important to be aware that the general principles and various detection techniques of Flowmon ADS allow a way to detect malicious activities, even without knowing their signature or behavior pattern.
3. Special thanks
Special thanks to the ALEF Distribution HU team and Mr. Tamás Szelinger for providing us with this example.
If you want to read more information about anomaly detection, please check the related link of Flowmon ADS. You can also try our online demo or download a free trial.
