Secure File Transfer: The Beauty of Managed File Transfer (MFT) Solutions
For enterprise-scale secure file transfers, Managed File Transfer (MFT) is the only way to go.
Let’s say you have one file you want to transfer securely. There are ways to do that, such as encrypting the file and sending it directly to the recipient who knows it is coming, can decrypt and will work with it safely. Now imagine trying to scale that across an enterprise and apply that approach to scads of regularly transferred files. How much does your head hurt (and heart ache) just thinking about it?
What is Secure File Transfer Anyway?
Most people don’t worry about the security of the files they transfer. Those charged with moving lots of files, handling sensitive information or dealing with compliance must consider security.
To be truly secure, a file or document must be fully protected during the entire transfer process. That means it must be encrypted at all stages including at rest. But how do you know the file made it to the right person? Do you know how many files and documents are sent to the wrong address? Too many to count.
To stop all that, the transfer itself should be tracked ensuring it happened properly. In addition, anyone accessing the file transfer system should be authenticated, preferably through multi-factor authentication. We mentioned tracking, and this should be brought to a higher level where all your file transfers are audited and logged so there is a complete record of all movements and any issues related to these transfers.
The Managed File Transfer (MFT) Answer
So how do you encrypt, track and authenticate file transfer users? Managed File Transfer (MFT), that’s how.
Because it can do all these things, MFT is the perfect way to replace all or most of the ways your shop currently transfers files, apart from the ad hoc sending of non-sensitive material.
Even better, managed file transfer is a true IT tool offering a single, secure, manageable and automated solution. And the MFT console gives IT pros a single pane of glass to see all activities, dramatically reducing the risk of file transfers gone wrong and offering quick and accurate answers if they somehow do.
That single solution for secure transfer and sharing of sensitive files has a number of benefits. End users and IT are more productive because regularly scheduled file transfers are automated so users don’t have to lift a finger and are secure in the knowledge the files will be taken care of properly.
Learn more about secure file transfer by reading Osterman Research’s What Decision-Makers Can Do About Data Protection report.
Why File Breaches Matter
Files are what many hackers are really after—after all, files are where the data is. The graph below from Osterman shows the types of commonly breached data, and how often breaches occur.
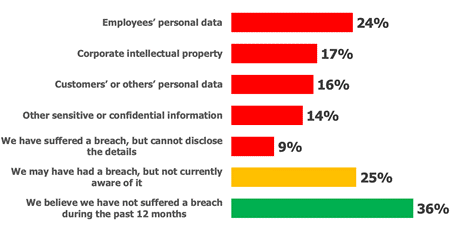
The top four categories of breached information types all represent a security and probable compliance disaster if breached, and all four are commonly held in files.
Many data breaches happen when files are moved within your organization or to partners and other organizations with a vested interest. These breaches come with GDPR investigations and often crippling fines. With Managed File Transfer (MFT), you can establish secure collaboration and automated file transfers of sensitive personal data. These files are not only moved safely, but they also include encryption and activity tracking to ensure compliance with GDPR, as well as PCI and HIPAA.
By default, all files sent outside of the company should be handled in a secure and trackable way—which is MFT.
With Managed File Transfer, you no longer rely upon your employees emailing personal data to other employees or outside entities or using insecure file sharing services. At the same time, you eliminate user errors and can track and report the details of every file transfer.
What Not to Do: Shadow IT
Many think DropBox and other file-sharing apps are pretty sweet—and they sure can be. For simple sharing of non-sensitive files, they are great. Just not for enterprises and the sensitive data they contain. Unfortunately, many enterprise employees use the DropBoxes of the world to send YOUR data. Don’t forget: These apps are for file sharing, not serious file transfer.
These unauthorized apps are also a breach and compliance fine waiting to happen. “Shadow IT services, the use of personal devices, the adoption of a 'cloud-first' or 'cloud-only' strategy, and merger and acquisition activity, among others, represent a collection of other threats to data protection. Decision-makers must evaluate the relevance and magnitude of these threats and develop appropriate countermeasures,” Osterman argued.
Those that fail to stop Shadow IT often pay the price. “The use of Shadow IT apps and cloud services results in confidential data being stored in systems with unknown security protections, the usage of apps that were never designed with business purposes in mind, and threats of unpatched and unidentified software vulnerabilities leading to data breaches. As employees embrace cloud applications beyond the list of corporate sanctioned services, inadvertent and malicious data leakage increases, along with unauthorized access to sensitive corporate data,” Osterman cautioned. “Shadow IT services that are not connected to the identity and authentication solution of the organization can also support malicious insider data theft. For example, revoking a user’s identity on their departure or termination will prevent future access to services connected to the identity solution, but for non-connected shadow IT services, no such prevention is possible. An ex-employee can continue to log in and access current and new data stored and shared through these services.”
External File Transfers Pose a Particular Data Risk
Your company needs to communicate with the outside world, and that includes sending important pieces of information in the form of files to external entities. Unfortunately, these files can be intercepted by cybercriminals, but also subject to other forms of unauthorized access or simple end user mishandling which opens the file up to those that should not see it.
Many companies try to secure external data transfers by creating policies that warn end users of the dangers of using file sharing solutions they believe to be secure, such as FTP (File Transfer Protocol) systems. Neither of these offer the security compliance demands. The best option is a secure MFT software solution such as MOVEit from Progress.
MOVEit Managed File Transfer tracks all file transfer activities, including authentication actions, in an archivable database.
With MOVEit Managed File Transfer, your end users can stop relying on insecure methods to share your company’s most precious and regulated information. Meanwhile, workflows and automated file transfer tasks accelerate your data sharing process while eliminating user error.
Learn About Data Protection from the Osterman Experts
Discover what data protection is all about from the experts at Osterman in the What Decision-Makers Can Do About Data Protection guide, then learn from Progress how MFT locks down sensitive data. In this guide, Osterman Research shares what security leaders should be focusing on and how to prepare your organization for total data protection.
In What Decision-Makers Can Do About Data Protection, you will learn:
- Areas of concern for decision-makers
- How to protect data loss by employees
- What decision-makers should do to protect data
- And more!
You can also check out our Top Methods for Secure File Transfer blog.
Finally, dive deep with our Managed File Transfer Buyers Guide.

Doug Barney
Doug Barney was the founding editor of Redmond Magazine, Redmond Channel Partner, Redmond Developer News and Virtualization Review. Doug also served as Executive Editor of Network World, Editor in Chief of AmigaWorld, and Editor in Chief of Network Computing.
