What is Hidden in Encrypted Internet Traffic Streams

Full internet encryption is on the horizon and with it the risk that hackers will gain access to your computer network.
When you open any website today, it is highly probable you will see a small padlock in front of the address. For the everyday internet user, this is the only visible sign that the site is secure and communication with the site is encrypted.
While less than half of internet traffic had been encrypted by 2017, today this figure is close to 80%.
But what does this trend mean for the people responsible for the security of technology, risk management and overall traffic? And new concerns have emerged since encryption can complicate or completely incapacitate traditional security technologies such as firewalls, which can look into data. If firewalls cannot see data packets as they did in the past, they definitely cannot protect networks and computers from malware.
According to the Ponemom Institute, encrypted traffic was in the previous 12 months used to spread about half the attacks by hackers. The problem is that while the percentage increase of encrypted traffic slows when it approaches 100 percent, there is a sudden growth of threats in encrypted communication and at the same time their sophistication grows as well. Cloud provider Zscaler blocked 1.7 billion (283 million monthly) threats hidden in encrypted communication in the second half of last year. Most of these attempts involved phishing, with over a 400% year-on-year growth. Others threats included botnets and attempts to exploit the operating system or other software vulnerabilities.
Encrypted traffic analysis
At the start of 2019, Flowmon added into its portfolio visibility into encrypted communication, which brought a breakthrough to the industry. Flowmon also developed other methods to analyse encrypted communication by finding patterns and the characteristics of malicious behaviour when malicious code (malware) hides in such communication.
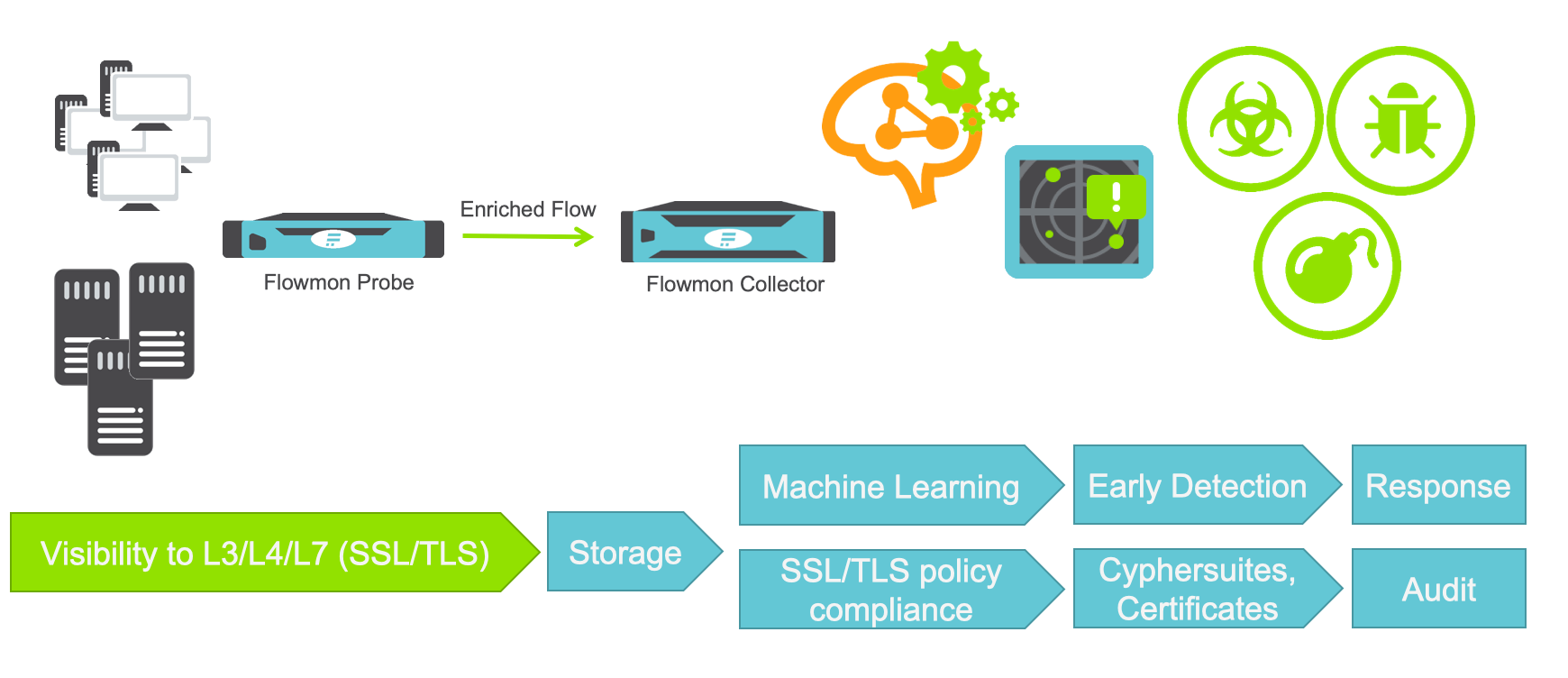
How it works:From the beginning to the end of the TLS handshake, making connections and exchanging encryption keys and certificates, Flowmon can collect all encrypted communication parameters such as TLS server version, TLS cipher suite, TLS server name indication, TLS client version, TLS certificate issuer common name, TLS subject common name, TLS public key algorithm, TLS certificate validity until, TLS JA3 fingerprint and many others. Thanks to this information, we can perform many operations and analysis on this data, consequently, the system can also warn us of any changes or particular events through automated alerts, with the execution of various actions (send email, run user script, send syslog or snmp trap,…).
Analysing JA3 fingerprints
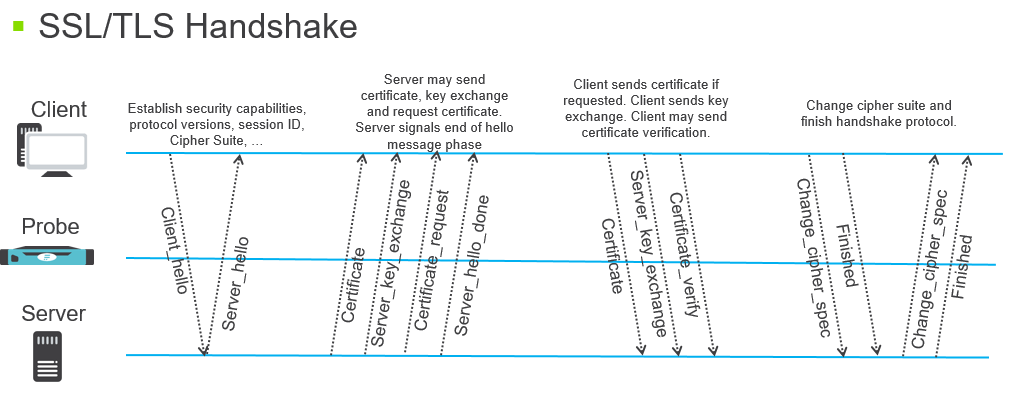
JA3 is a method for creating SSL/TLS client fingerprints that are easy to produce on any platform and can be easily shared for threat intelligence. TLS and its predecessor, SSL, I will refer to both as “SSL” for simplicity, enable encrypting communication for security reasons, but also allow attackers to hide malware. To initiate a SSL session, a client will send a SSL Client Hello packet following the TCP 3-way handshake. This packet and how it is generated depends on packages and methods used when building the client application. The server, if accepting SSL connections, will respond with a SSL Server Hello packet that is formulated based on server-side libraries and configurations as well as details in the Client Hello. Because SSL negotiations are transmitted in the clear, it is possible to fingerprint and identify client applications using the details in the SSL Client Hello packet.JA3 is a much more effective way to detect malicious activity over SSL than IP or domain based IOCs. Since JA3 detects the client application, it does not matter if malware uses DGA (Domain Generation Algorithms), or different IPs for each C2 host, or even if the malware uses Twitter for C2, as JA3 can detect the malware itself based on how it communicates, rather than what it communicates to. This is a straightforward way how to use Flowmon to find possible threats in connection with detecting specific JA3 fingerprints.
Use cases in Flowmon monitoring centre
Freely accessible sources are adequate enough to collect information about specific JA3 fingerprints that are of our interest and that we would like to monitor; we can then analyse the collected data directly by analysing and filtering the FMC using the "tls-ja3" parameter that filters out the communication where the fingerprints are located. A more sophisticated solution, however, is to create a profile that will offer us, on a daily basis, results from live data.Profile filled with JA3 fingerprints of specific malicious codes:
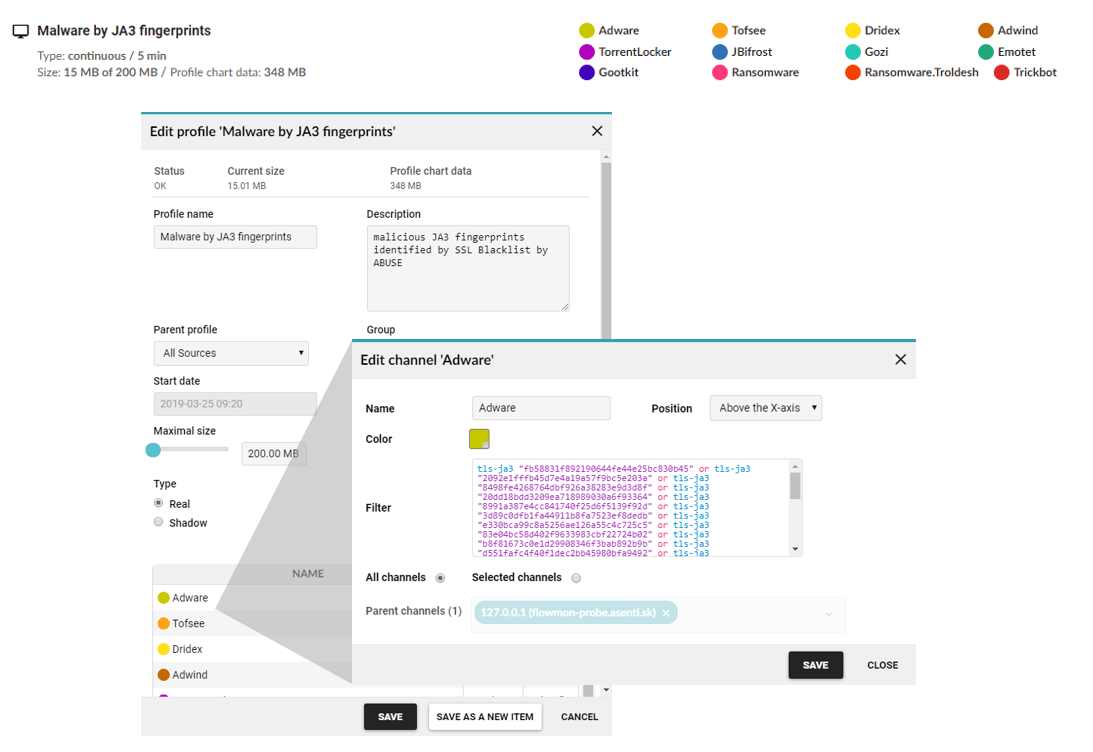
The profile created in this way would offer results in the form of a visualised output, which could also be sent as a PDF report on a daily basis, or in this profile you could enter an alert that could take some specific action:
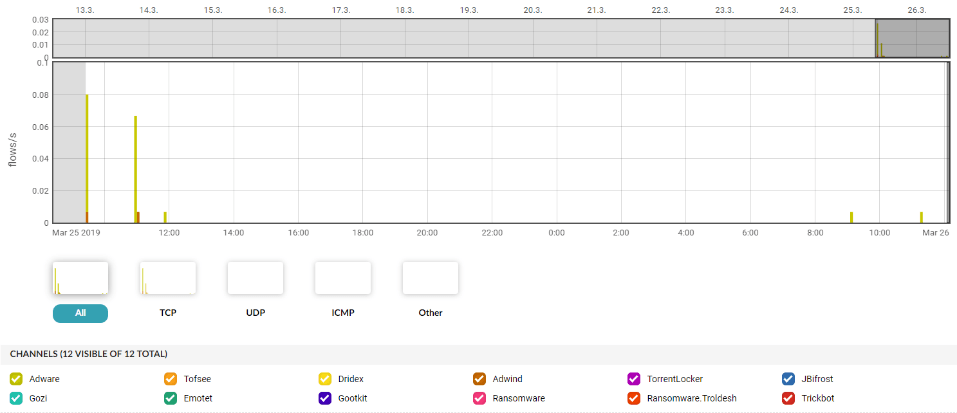
Alerting in the case of monitoring encrypted traffic
Many companies which want to have secure transmission of information while communicating to their internal systems, but also those who use websites for their presentation, use certificates to secure a HTTPs’ communication, issued by a certification authority, for a given time period. The task of the organisation is to monitor the validity period of the issued certificate to prevent data being unsecured for a period of time. With Flowmon and its visibility into encrypted communication, we can notice the date when the certificate expires. In connection with the possibility of alerting and setting the alert correctly, it would never happen again that this type of communication would be unsecured for a certain period of time, because the system can notify us early enough about a certificate expiring, or even that our network uses weak TLS 1.0 encryption, so we can take corrective measures well in advance.
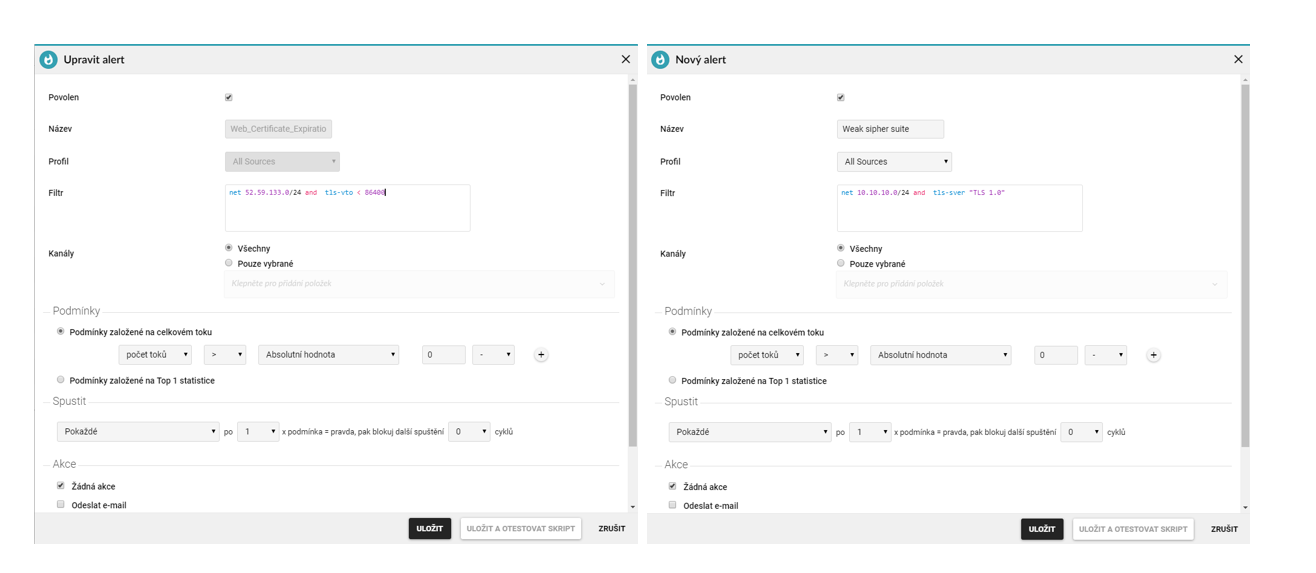
An alert that in the given segment of the network notifies you about a certificate expiring some 24 hours earlier than UNIXTIME, or an alert that tells us where weak encryption is being used in a network segment.
Summary
Clearly for reliable threat protection, organisations will eventually need to incorporate new protective means based on behavioural analysis, the use of artificial intelligence, and visibility into encrypted real-time communications. These tools promise to detect malware in encrypted traffic in real-time and crucially without reducing network throughput and application performance.The expansion of existing security strategies will not be necessary just to know what hides in encrypted communication, but also to have the opportunity to stop various threats, such as man-in-the-middle attacks or data theft attempts.New technologies will also be important for auditing, as they allow the detection of communications that use security certificates that are not up-to-date or compatible with corporate policy. Additionally, new technology will allow a way to control the strength of encryption, and find other vulnerabilities related to data encryption. Most organisations do not have a similar overview today other than using very laborious and time-consuming methods.
