What is New in Flowmon 12.2 and ADS 12.1

Our development teams continue to improve Progress Flowmon. The latest update takes the core Flowmon product to version 12.2, while our industry-leading Anomaly Detection System (ADS) gets incremented to ADS 12.1.
In this blog, I'll call out the most important changes, additions and improvements, while the full details of features and benefits of Flowmon solution are available on cyber security page and network visibility page.
Flowmon 12.2 Highlights
Here are some of the highlights from the latest Flowmon 12.2 release.
FIPS-Compliant Remote Access
In this version of Flowmon, we have adjusted cipher suites for remote access to Flowmon appliances to comply with FIPS (Federal Information Processing Standard) requirements. While FIPS started as a US government standard for specifying computer security cryptographic levels, its assurance of the highest level of privacy and security has led to its adoption far beyond federal use and the USA.
The FIPS support in Flowmon 12.2 includes:
- SSH access to a Flowmon appliance (Probe and Collector) protected by a FIPS-approved security algorithm.
- Web (HTTPS) access to a Flowmon appliance (Probe and Collector) protected by a FIPS-approved security algorithm.
More details on the FIPS-compliant ciphers and cryptographic algorithms used in this feature are detailed in the latest Flowmon User Guide under the Setup & Configuration section.
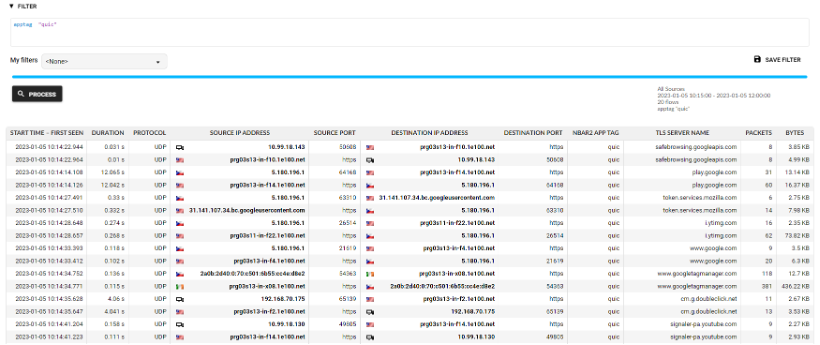
QUIC Protocol Visibility
Support for QUIC (Quick UDP Internet Connection) has been added in this release. IT professionals can identify QUIC traffic in their network and extract SNI (Server Name Indication) information like they are used to for legacy web traffic. This is increasingly common for access to websites like search engines, video streaming sites or from mobile devices where delays can be a significant issue. QUIC is turned off by default in Flowmon 12.2, but Administrators can enable it in the advanced settings of monitoring ports. The image below displays visibility into QUIC protocol.
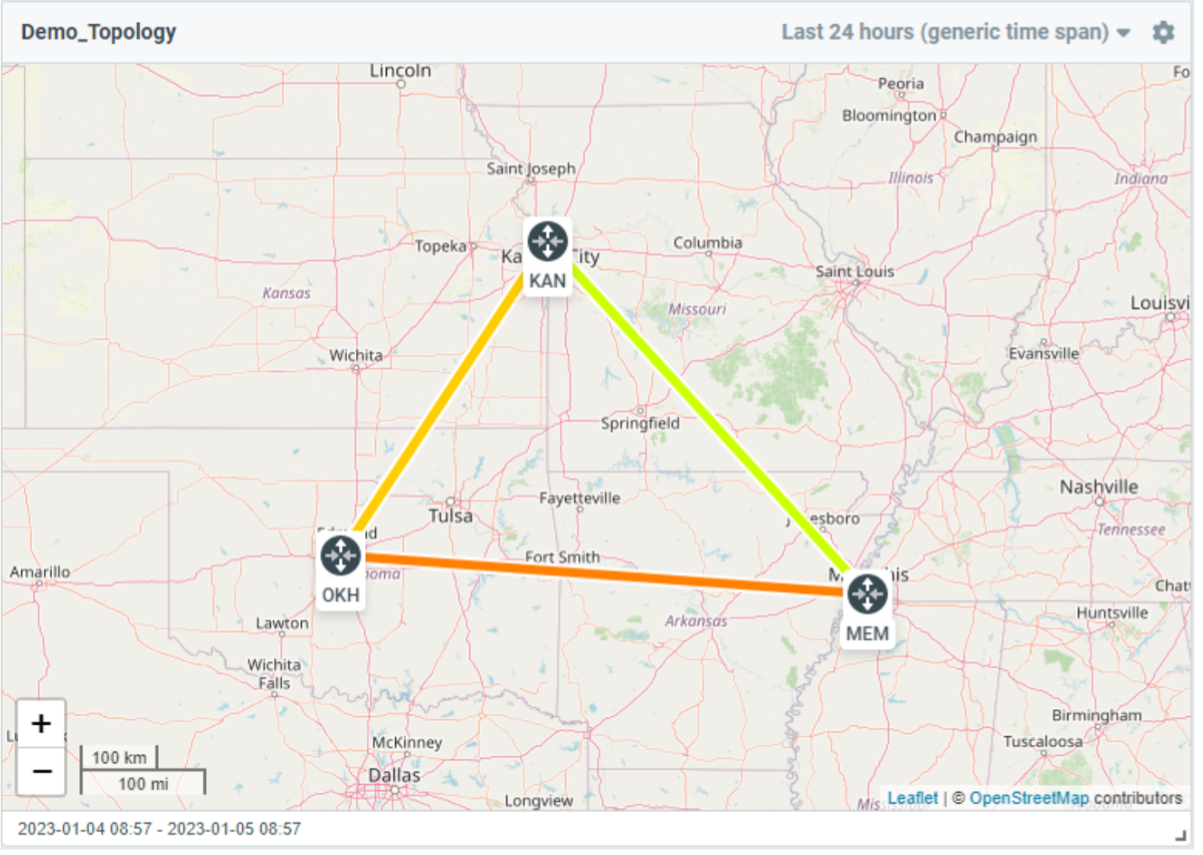
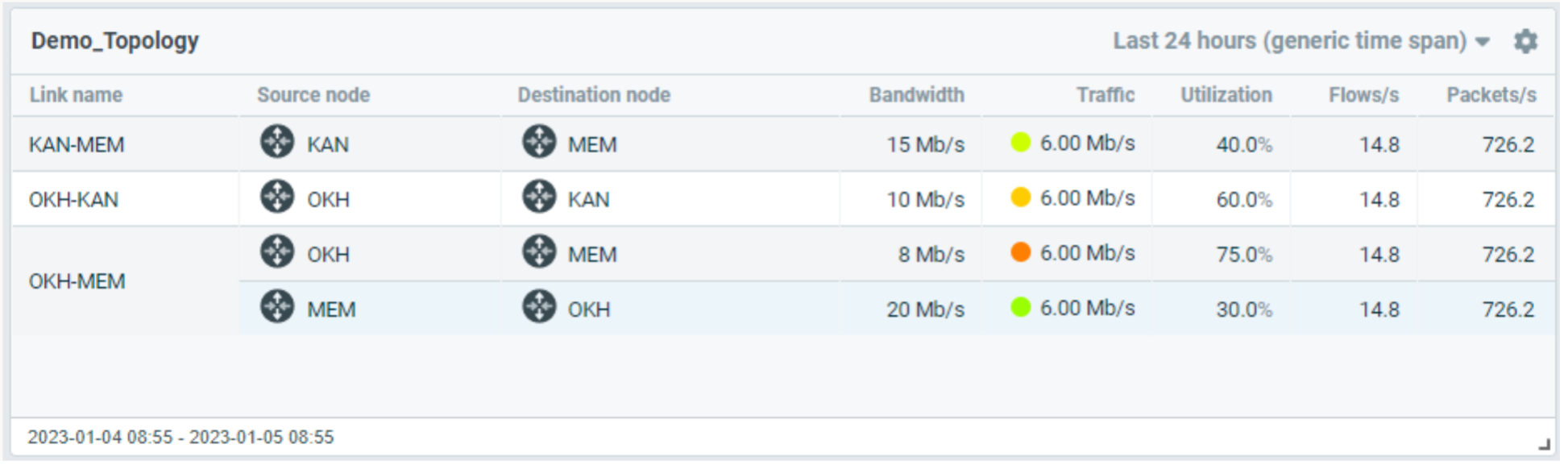
New Table Widget for Topology Maps
Flowmon 12.2 makes alternative visualization of topology maps available in the form of a table, showing bandwidth congestions and high link utilizations. Utilization is calculated from the bandwidth for given time period, given capacity and expressed in percentage. While the topology map view is the preferred option for dashboards, table view provides a comprehensive understanding of bandwidth utilization in reports.
Distributed Architecture (DA) Improvements and Fixes
Working with large volumes of logs was unintuitive and problematic in previous versions of Flowmon. In the 12.2 release, several DA improvements make the downloading, transfer and analysis of large volumes of logs much better.
Examples of the improvements include:
- Asynchronous access - log processing and downloading can now happen in the background with notifications for when logs are ready to access.
- The latest available logs are gathered together and accessible in a single location.
- The UI now shows the date of the latest logs.
- Logs are now stored in a more a suitable location to prevent overloading the home directory on disk.
- DA instances that logs get downloaded from can be selected.
- Logging exception errors are improved across the board.
In addition to the log processing improvements, the DA experience has been improved by the following features:
- The same global ID now identifies all users on multiple DA instances in a backwardly compatible way that doesn't break existing modules or the REST API.
- Improved error reporting when there is an issue installing on DA Units. The installation process will halt and report a specific error code when there is an unassigned unit in the DA topology. This will prevent incomplete deployments due to individual units failing to install.
Updated to use Progress Branding
We have taken the opportunity of this release to update the Flowmon product line to use the branding, colors, logos and icons used across the Progress product family.
Additional Changes
Additional changes to Flowmon 12.2 that are worth calling out include the following:
- Reporting removed from Flowmon Monitoring Center (FMC) - Reporting functionality was introduced as part of the new Dashboard and Reports module some time ago, with the intention of replacing the previous reporting functionality in FMC. Reporting in FMC has remained available to allow time for migration and adjustments. Flowmon 12.2 removes the reporting functionality from FMC allowing you to use the Dashboards and Reports module for all your reporting needs.
- Notifications about the end of support for SP, FR, and GR localizations - Support for Spanish, French and German localization is scheduled to end with Flowmon v13. As a result, the 12.2 release includes notifications for users using these three languages, informing them about the forthcoming change.
- Package update process improvements - A new dynamic progress indicator is presented when a non-DA update installation happens on a Flowmon instance. The new indicator displays the installation progress for both the Flowmon package and any modules. Flowmon is also switched to maintenance mode during upgrades to prevent an unintentional reboot or shutdown.
- Configurable session timeout to log out an inactive user - In the past, when a user had closed their browser window without logging out of a Flowmon session, there was a hard-coded grace period of 10 days during which they could reestablish a session without having to authenticate again. Many organizations have requested that this duration should be a customizable setting to allow compliance with security policies. In Flowmon 12.2, User Session Timeout is configurable and has a default setting of 12 hours. Additionally, the REST API access token is also configurable and has a default of 24 hours, as does the REST API refresh token timeout which defaults to 48 hours.
- Flow data timestamp adjustments - Some 3rd party routers and switches issue unreliable flow data time stamps (e.g. relative timestamps without reporting systime). This can wreak havoc with accurate flow data monitoring and analysis. In Flowmon 12.2, there is now an option to adjust the flow start time issued by routers and switches and replace it with timestamps calculated by Flowmon using flow receive time and flow duration.
- Last packet saved – If an issue occurs, that would cause the Flowmon Probe process that is monitoring the network traffic to crash and the last packet will be saved to provide data for further analysis.
ADS 12.1 Highlights
There are also three improvements to ADS 12.1 that we want to highlight.
A New Detection Method for DoH Traffic
DNS over HTTPS (DoH) poses a substantial risk to company security by bypassing enterprise DNS servers and DNS-based services to filter potentially malicious traffic, thus leaving devices unprotected. In ADS 12.1, we introduced a new detection method to identify and report on the use of DNS over HTTP (DoH) by individual network devices enabling network administrators to identify and locate specific devices using the encrypted DNS protocol. This makes it much easier to reduce the overall risk and detect malicious activities or communications that cybercriminals try to hide by using encrypted DNS.
Improvements to Existing Detection Methods
We always listen to customer feedback on how we can improve the Flowmon solution to make network administrators' lives easier and help them monitor and protect their organization's networks. In ADS 12.1, feedback has led to improvements in several detection methods.
- RDPDICT: This detection method highlights attacks on the widely used Remote Desktop Protocol (RDP) service to gain unauthorized access to a service or misconfigured device. This method is revised in the latest release to detect attacks against the current & recent versions of RDP protocols. New method parameters also allow admins to tune the detection to their environments.
- TEAMVIEWER: This is a method used to detect the use of the remote access application. The method's accuracy will increase due to using Autonomous System Numbers (ASNs) as part of the analysis.
- DNSANOMALY: The ForbiddenServer sub-method within DNSANOMALY now allows the exclusion of local DNS servers. This will reduce the number of false positives when a local DNS server communicates with public DNS servers.
- BLACKLIST: The IP blacklist format has been extended to include a comment field. This optional field provides additional information about blacklisted IP addresses and helps users understand the context as well as document why a particular IP address is on the list.
Improved Analysis & Workflows
We have streamlined the activities needed within FMC when investigating an event. In previous releases, a manual process required investigators to copy filter from ADS and paste it to FMC. Then you had to manually find the relevant traffic segments in FMC, select and confirm the channel and time interval, apply the filter you wanted and then start the analysis of the event data.
We have listened to your feedback, and in ADS 12.1 all these tasks are now grouped together in a preconfigured FMC analysis screen where you can get to work immediately. Example below shows the direct link in event evidence.
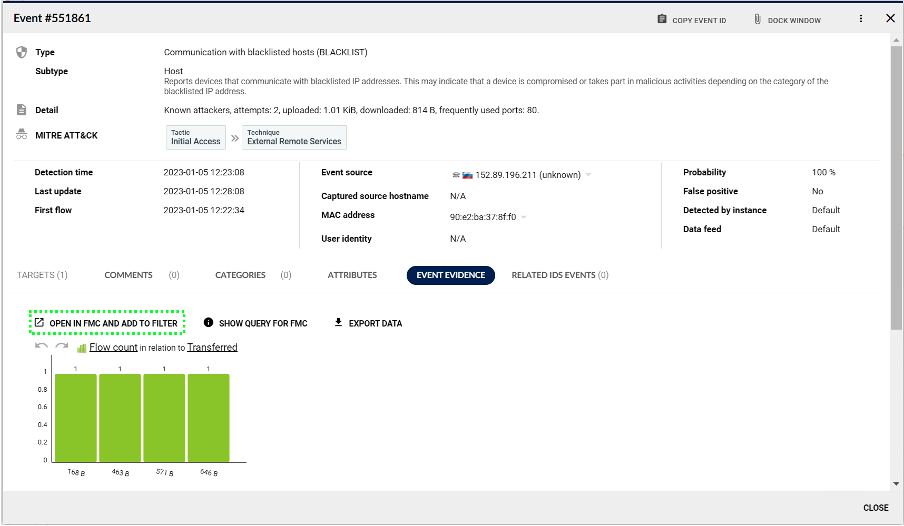
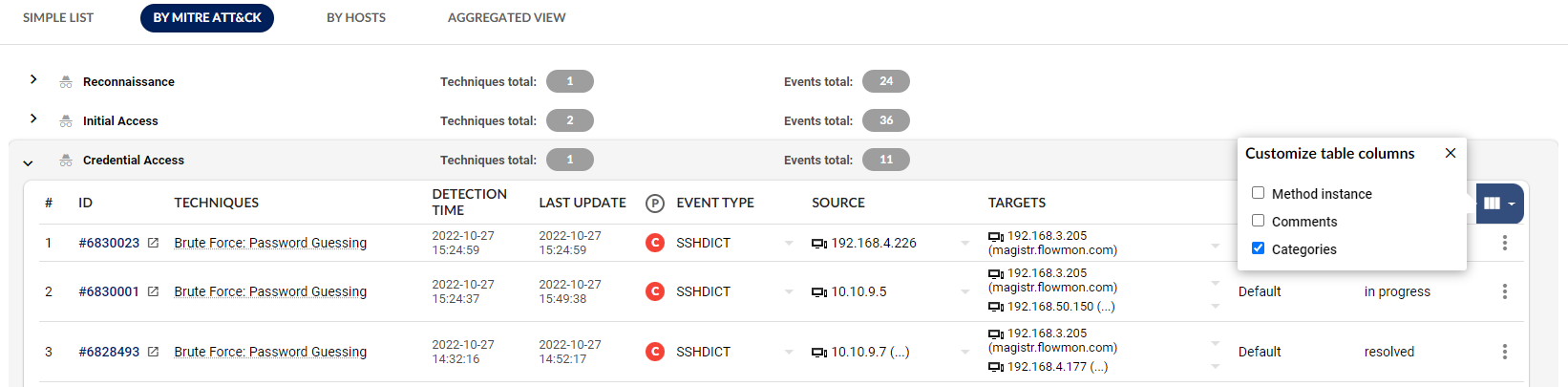
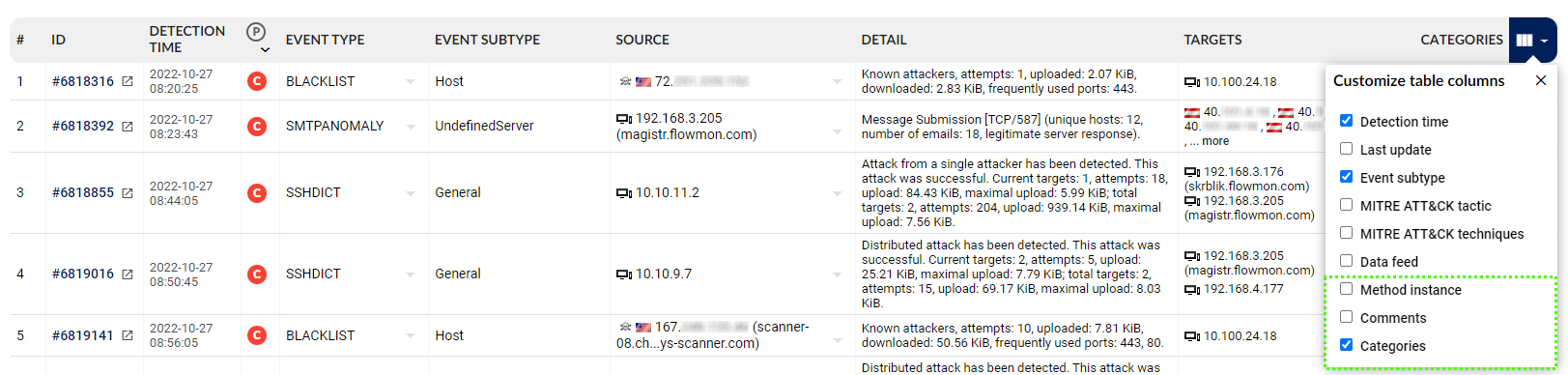
And last but not least, we are expanding the available columns that user can configure in his views. Cybersecurity engineers face the problem of prioritizing and understanding the status of existing events on the ADS Analysis and ADS Events page, while the information about the status is hidden in Event details. In the past, a user usually had to work around this by pressing each event separately which took a lot of time.
To improve the workflow, users can now customize columns with Method instances, Comments and Categories in the IP view in the Analysis page as shown on picture below.
Users can also add new columns with ‘Simple list,’ ‘By MITRE’ and ‘By Hosts’ tabs in the Events page. An example of a brute force attack viewed “By MITRE ATT&CK” tab in the event page is shown below.