Accelerate Network Detection, Respond Quickly and Efficiently
AI-Powered Cybersecurity Solution of Choice
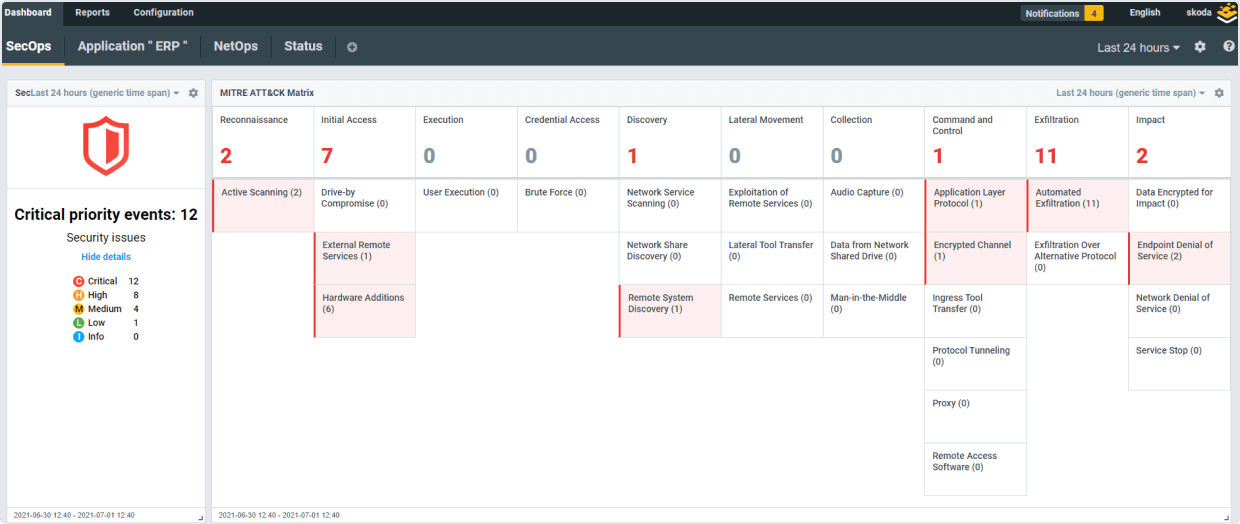
Progress® Flowmon® Network Detection and Response (NDR) is the first line of defense, integrating AI and Intrusion Detection Systems (IDS) to reduce noise, automatically prioritize tasks and helps you minimize data breaches.

Enterprises You Trust Use Flowmon





Detect Ransomware, Expose Insider Threats, Respond Immediately
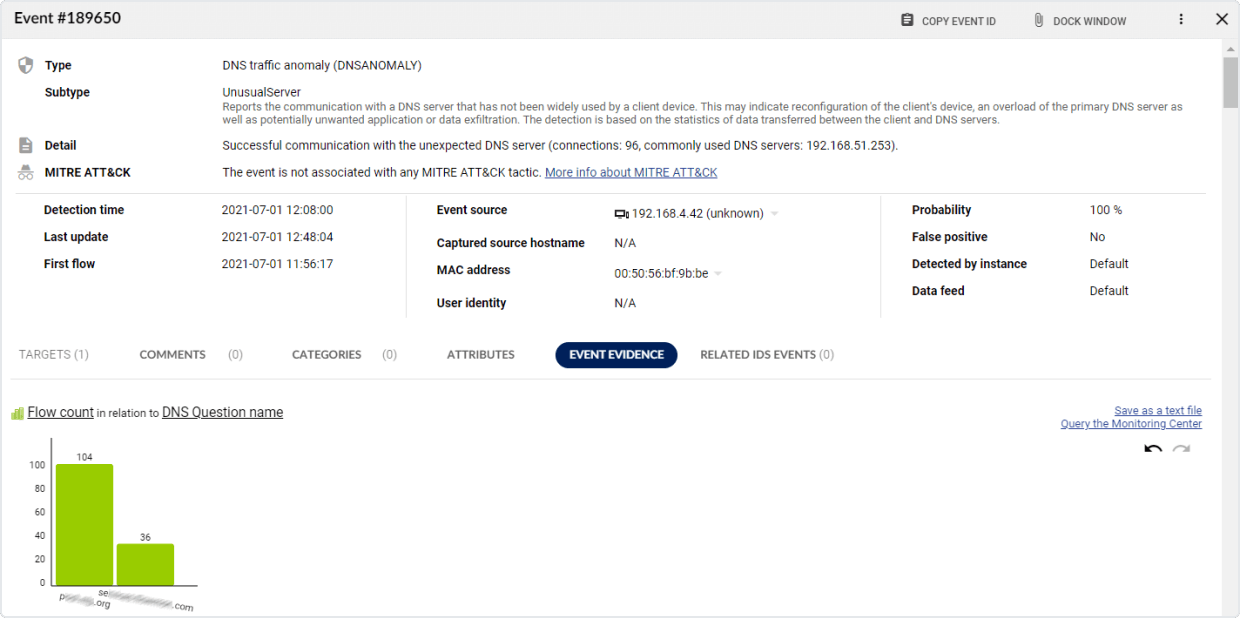
- Real-time network behavior analysis and enterprise-grade anomaly detection system
- 40+ detection methods and 200+ algorithms to detect data breaches at any stage
- Detection of rogues, insider threats, zero-day exploits, ransomware, and targeted attacks
- Reinforce your security matrix via integration with log management, SIEM, SDN, incident response, etc.
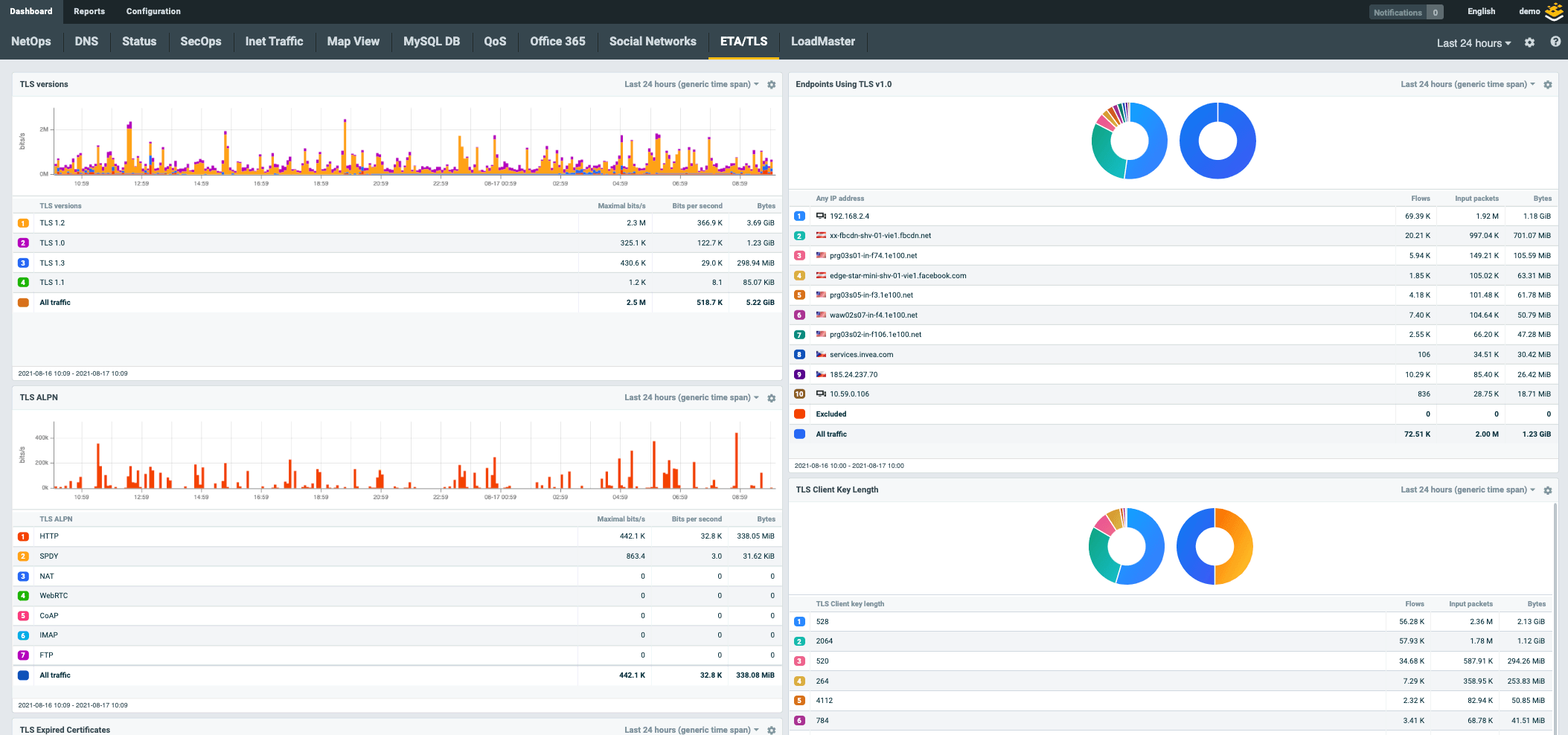
- Comprehensive visibility across on-premise, hybrid, and cloud environment at scale
- Combining AI capable of tracking unknown threats with signature-based intrusion detection and threat intelligence for known attackers and malware
See Live Product Demo
Explore a fully interactive product of Flowmon and see what issues it can tackle.