

Flowmon NDRA Scalable ExtraHop Alternative for a Fraction of the Price
Flowmon offers deep network insights and mature network detection and response capabilities while remaining highly scalable and cost-efficient.

Enterprises You Trust Use Flowmon





Flowmon Technical Features
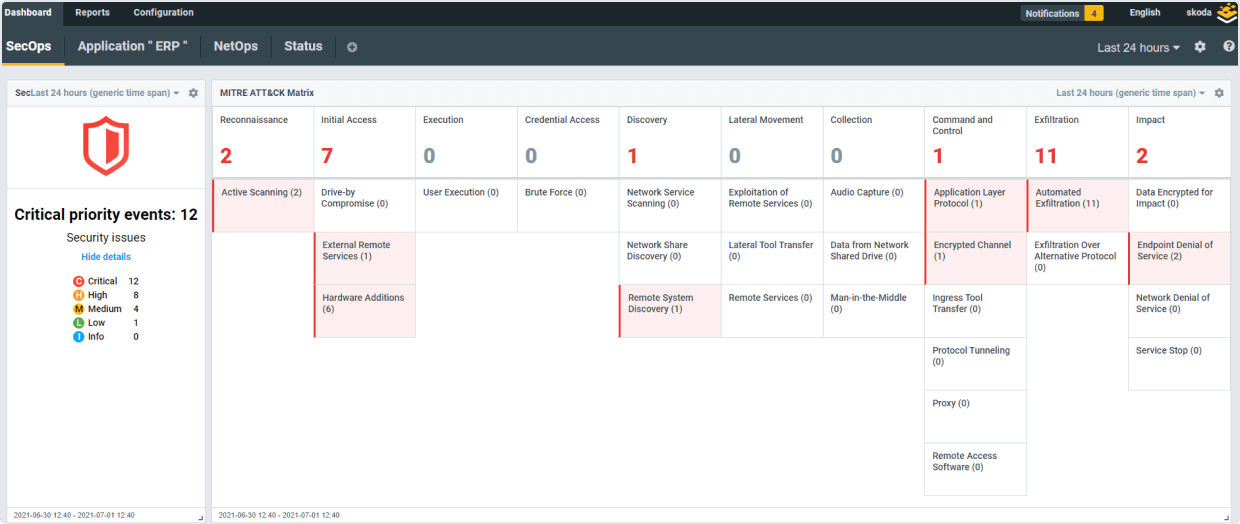
Instant Threat Detection
Kemp Flowmon features over 40 detection methods and more than 200 algorithms to pick up subtle changes in network traffic and expose the malicious activity of unknown and insider threats operating in the network including encrypted traffic. In addition to signatureless detection, it leverages the signature-based Suricata IDS and MISP threat intelligence feeds.
Respectful of Your Privacy
Flowmon does not rely on decryption to extract relevant insights. Instead, it uses non-invasive Encrypted Traffic Analysis, which is an efficient approach to detecting compromise as well as ensuring cryptographic compliance by analyzing network metadata. No data from your network goes for further processing to the cloud.
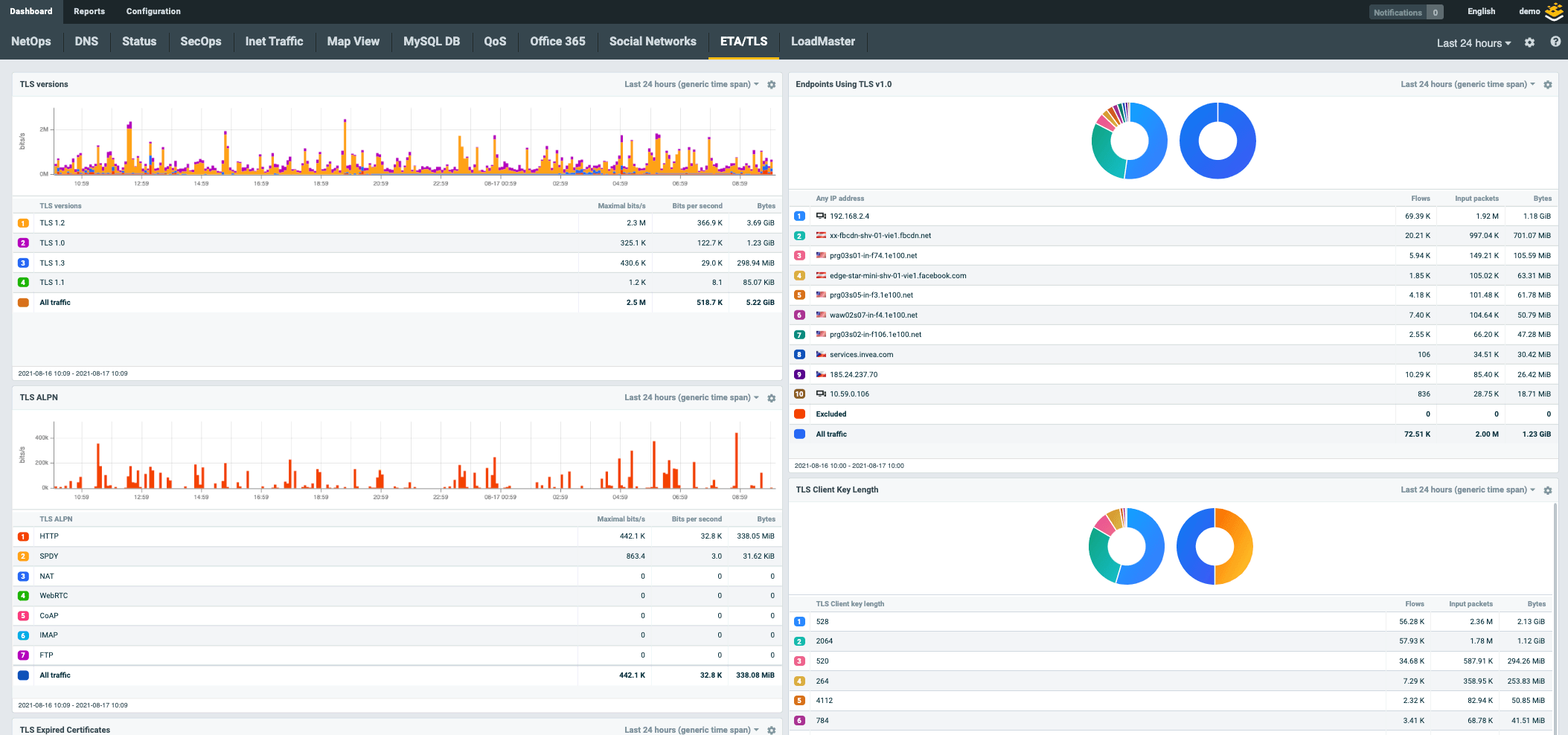
Future-Proof Technology
Besides low scalability, proprietary packet-based technology faces additional challenges with traffic encryption and hybrid deployments. Kemp Flowmon is flow-based (NetFlow/IPFIX) and thus perfectly suited to overcome these issues with zero impediment and deliver future-proof, cross-environment security that scales easily while remaining cost-efficient.

Compare Flowmon to ExtraHop
| Flowmon | Extrahop | |
|---|---|---|
NetOps functionalityInsights for effective network troubleshooting. | ||
Zero-day threat detectionLeverages behavior analysis for signatureless threat detection. | ||
Reasonable pricingCost-effective pricing plans that scale with your business. | ||
Simple deployment and licensingAll functionalities are delivered and managed via one appliance. | ||
Scalable technologyNetwork telemetry supported by on-demand packet analysis. | ||
Privacy-preservingThreat detection is carried out by your appliance (no cloud processing) and without decryption. |
Monitor network performance, expose threats, respond immediately
- Leverage advanced detection and response capabilities at a low cost.
- Scale up easily with futureproof technology for hybrid and multi-Gbps enterprise environments.
- Reinforce your security matrix via integration with log management, SIEM, SDN & incident response.
- Eliminate visibility blind spots by providing your network and security teams with a unified source of truth.
See Live Product Demo
Explore a fully interactive product of Flowmon and see what issues it can tackle.
Expose Unknown Threats Quickly and Efficiently
Get features packed solution with great support.
Maximize Investment
Flowmon is up to 500 times more scalable than packet analysis.
Solution Ready in Minutes
Get data on the dashboards within 30 minutes of deployment. No tedious configuration.
Top-Rated Support
Word-class 24/7 support with 5/5 ranking on Gartner Peer Insights.


