

Flowmon NDRScalable Plixer Alternative with Mature Threat Detection
Plixer's Scrutinizer offers a similar capability in NPMD, but lacks the mature threat detection capabilities. Flowmon offers deep network insights as well as advanced network detection and response capabilities while remaining highly scalable and cost-efficient.

Enterprises You Trust Use Flowmon





Flowmon Technical Features
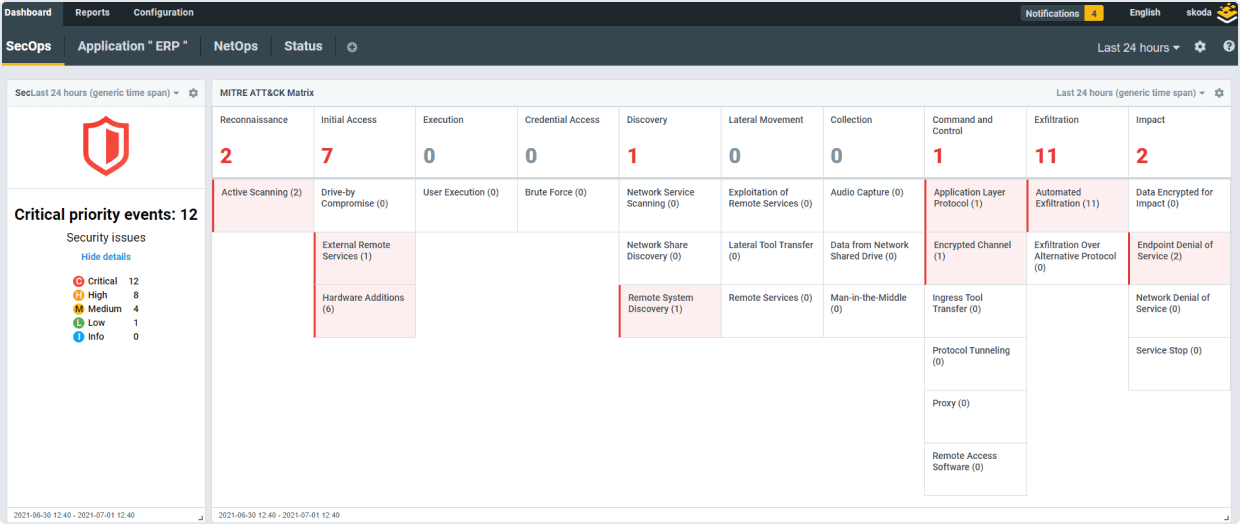
Instant Threat Detection
Kemp Flowmon features over 40 detection methods and more than 200 algorithms to pick up subtle changes in network traffic and expose the malicious activity of unknown and insider threats operating in the network including encrypted traffic. In addition to signatureless detection, it leverages the signature-based Suricata IDS and MISP threat intelligence feeds.
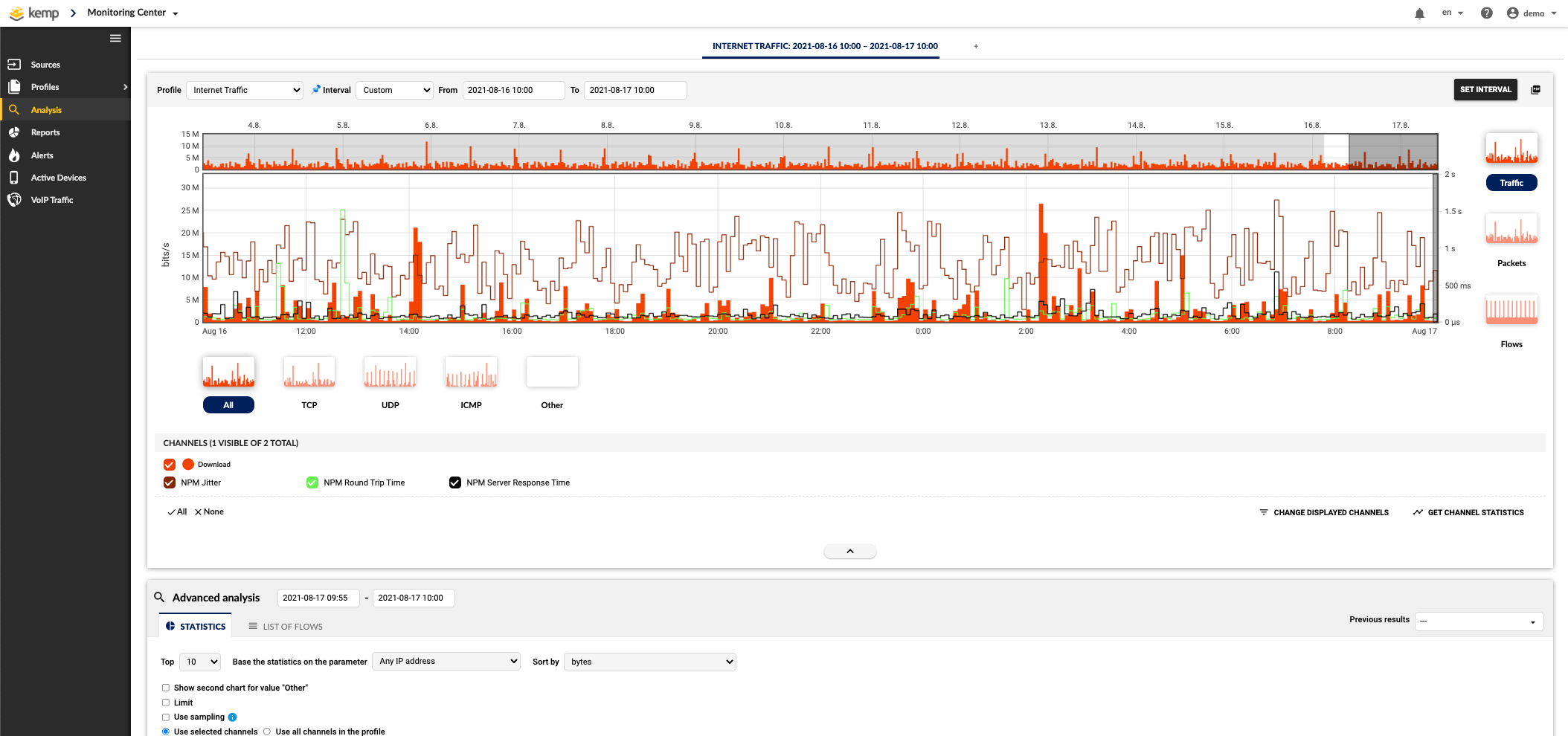
High Scalability & Long-term Storage
Small business or global distributed architectures – the scalability is limitless and always cost-effective with long-term storage access so you can benefit from weeks of historical traffic data storage without alteration to your pricing plan.
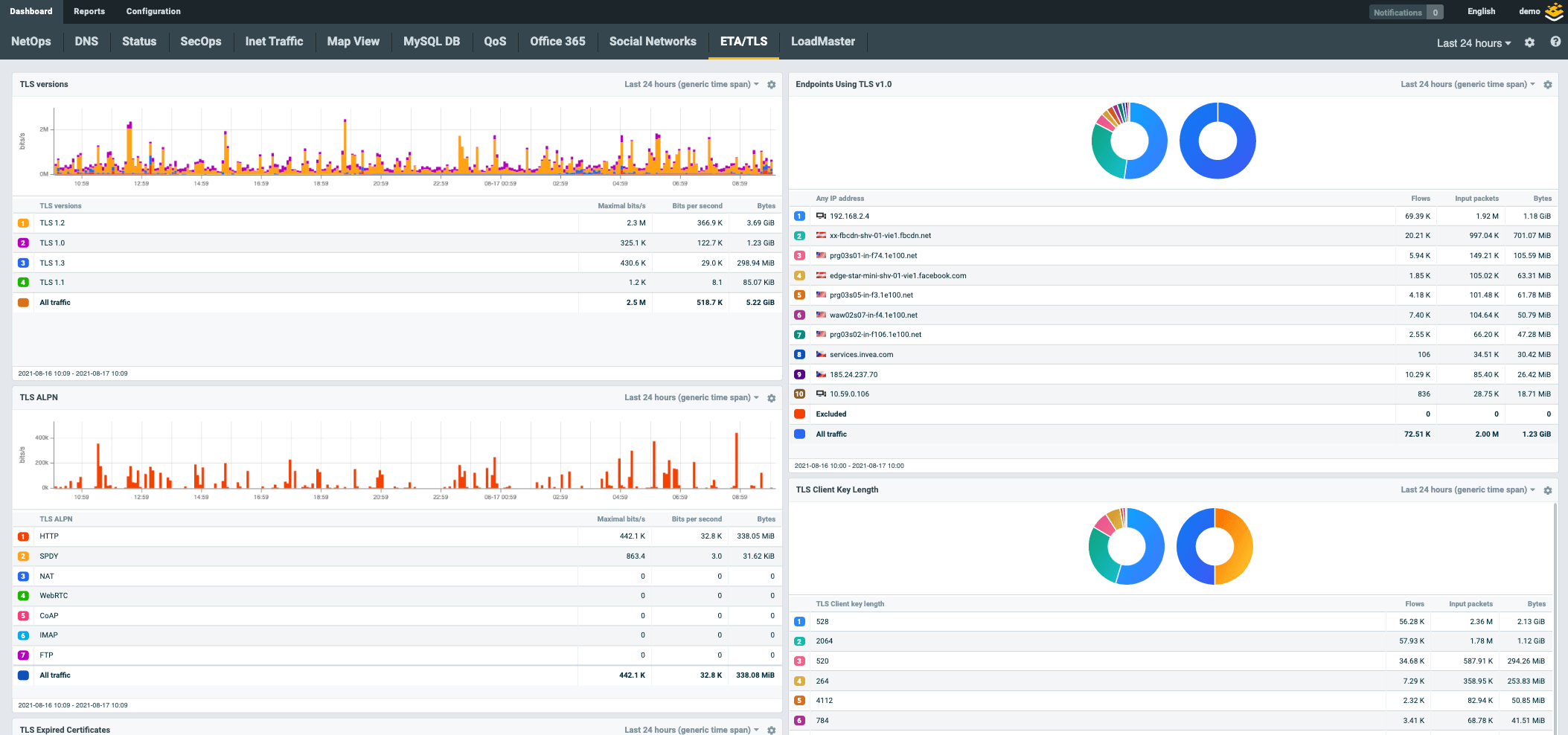
Future-Proof Technology
Business growth, the rise of traffic encryption, and the adoption of hybrid environments place challenges for NDR tools in terms of scalability, flexibility, and budgetary constraints. Flowmon is flow-based (NetFlow/IPFIX), which makes it well-equipped to cope with these challenges with zero impediment and deliver futureproof, cross-environment security that scales easily while remaining cost-efficient.
Compare Flowmon to Plixer
| Flowmon | Plixer Scrutinizer | |
|---|---|---|
Vendor-independentSupports multiple data formats from different vendors (IPFIX, NetFlow, sFlow, jFlow,…). | ||
One versatile applianceFlow collector, management console, add-on modules in one appliance. | ||
Automated threat detectionAnalyzes network traffic and alerts on suspicious anomalies. | ||
Adaptive baselining in security use casesReference values update dynamically over time without a manually pre-set threshold. | ||
On-demand Packet capture analysisLearn the root-cause of issues immediately thanks to triggered capture and automated analysis. | ||
User-defined behavior patternsDefine your own detection methods using SQL-like queries over flow data. | ||
Scalability up to 100GbProvides high performance up in multi-Gb/s environments. | ||
Signature-based detectionLeverage Suricata IDS and supplement an additional level of security. | ||
Scalable licensingOffers a fairer price for SMBs. | Licensed per flow per second | Licensed per the number of devices |
Monitor Network Performance, Expose Threats, Respond Immediately
- ML-driven network behavior analysis, signature-based detection, and threat intelligence feeds.
- MITRE ATT&CK tactic framework and technique visualization.
- Scale up easily with futureproof technology for hybrid and multi-Gbps enterprise environments.
- Reinforce your security matrix via integration with log management, SIEM, SDN, incident response, etc.
- A single source of truth for network and security teams across on-prem, edge, and cloud traffic.
See Live Product Demo
Explore a fully interactive product of Flowmon and see what issues it can tackle.
Speed up Your Incident Investigation and Response
NetSecOps
Flowmon provides insights relevant to multiple teams from one UI, fostering cross-functional collaboration and significantly cutting incident response time.
Cross-Environment Visibility
On-premise, edge, and cloud under one visibility umbrella. Advanced performance monitoring and diagnostics across all your environments and applications.
Flexible Pricing
Flowmon offers you more functionality under a more cost-efficient plan that scales with your business growth.
Expose Unknown Threats Quickly and Efficiently
Get features packed solution with great support.
Maximize Investment
Flowmon is up to 500 times more scalable than packet analysis.
Solution Ready in Minutes
Get data on the dashboards within 30 minutes of deployment. No tedious configuration.
Top-Rated Support
Word-class 24/7 support with 5/5 ranking on Gartner Peer Insights.

“After three months of intensive testing we were able to prove that Flowmon was the right product due to its performance, anomaly detection capabilities, scalability in GÉANT and its simplicity when managing and configuring.”
Wayne Routly
Head of Information & Infrastructure Security

