Mobile Device Management and Secure File Sharing: Strategies for Securing Mobile Data

The best mobile data strategies for companies with a bring-your-own-device policy pair mobile device management (MDM) with a secure file sharing solution.
Mobile security breaches are increasing, and global companies are especially at risk. The statistics are alarming. According to the Verizon Mobile Security Index (MSI) 2022 Report, almost half (45%) of companies surveyed suffered a security compromise involving a mobile device in the past 12 months, a 22% increase over the previous year. Of those respondents, 73% described the impact of the attack as major and 42% said that it had lasting repercussions.
It’s not hard to see why these breaches are on the rise. We see mobile devices used for more and more business purposes, and employees are taking them everywhere they go. The problem? Cybercriminals know that these mobile devices are a weak link in the corporate security chain (due to their inherent security challenges), and they’re actively exploiting it.
What can businesses do with their increasingly mobile workforce? How can they keep confidential files safe when employees are accessing and sharing them on smartphones and tablets outside office walls?
No need for panic. In this article, we’ll explore two key solutions that can help you better control mobile data security: mobile device management and secure file-sharing services. Keep reading to learn how to empower your mobile workforce without compromising security.
How BYOD Creates New Risks
The bring-your-own-device (BYOD) trend may be convenient, but it also introduces many new risks to mobile security. When employees access company data and systems from their personal smartphones, tablets and laptops, that data becomes vulnerable.
Cybercriminals know there is a lot of vulnerable data out there which is why malware, phishing and network attacks now target more mobile users. Companies are dealing with mobile malware infections daily. Phishing attempts via SMS, WhatsApp and other messaging apps are increasingly common. Unsecured public Wi-Fi networks are easy targets for hackers to steal login credentials and personal information. Social engineering tactics like fake apps, phishing links and tech support scams are also prevalent on mobile. Employees may install what they think is a useful app, only to have their data compromised. A single click on a malicious phishing link or text could infect a device and enable access to corporate systems.
Mixing personal and work accounts on one device creates complications. When personal apps have access to corporate data and systems, it’s difficult to enforce security controls. There are more opportunities for data leakage and account compromise. One way to better protect sensitive data is by employing a mobile device management (MDM) solution.
Implementing Mobile Device Management
Mobile device management was created to address security risks from employee-owned devices. MDM allows IT to control which devices access the corporate network, enforce security policies like strong passwords and remotely wipe data from lost or stolen devices. Some MDM solutions also provide secure web browsing and file sharing to help safeguard data in transit.
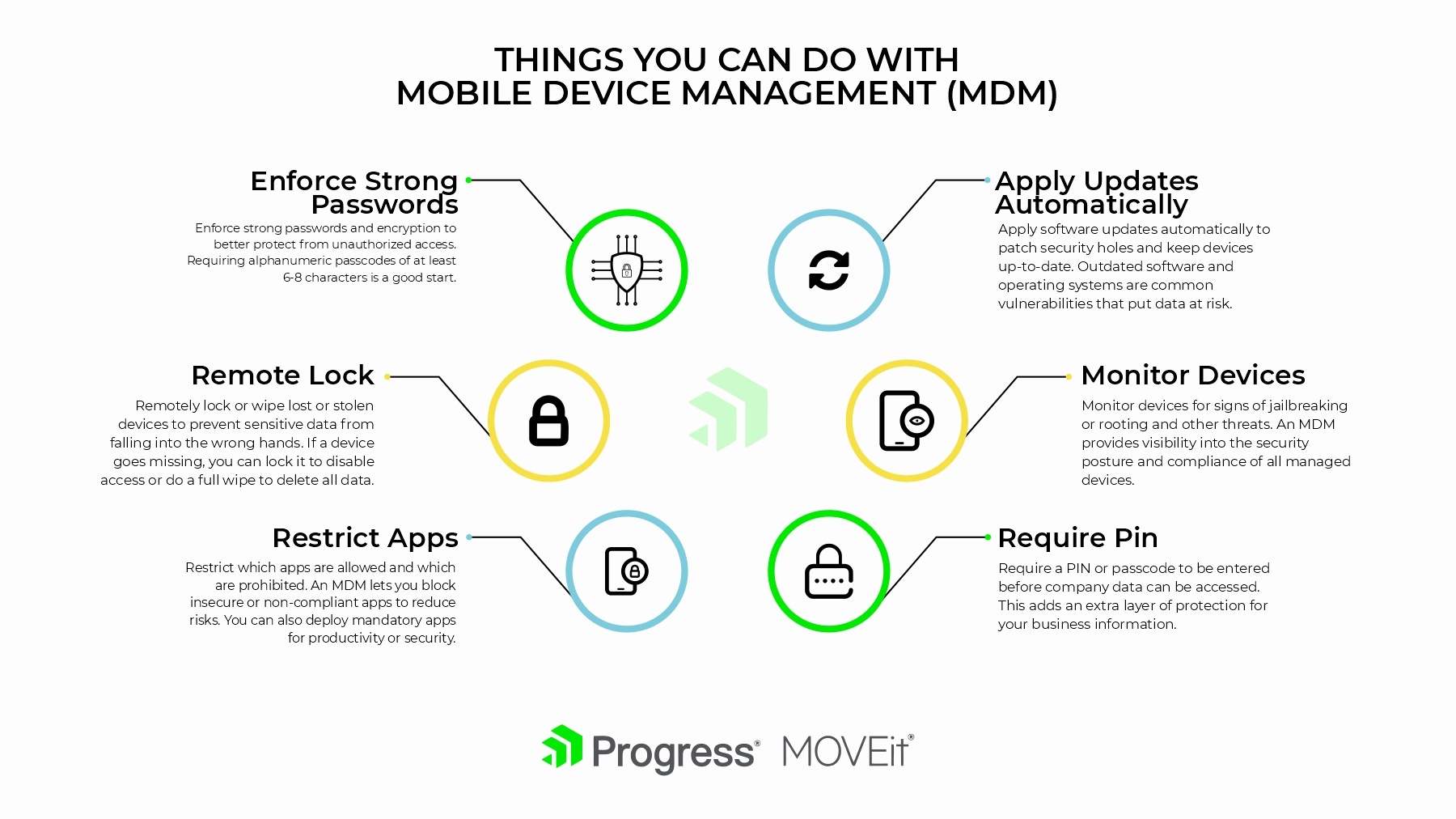
With an MDM, you can:
- Enforce strong passwords and encryption to better protect devices from unauthorized access. Requiring alphanumeric passcodes of at least 6-8 characters is a good start.
- Remotely lock or wipe lost or stolen devices to help prevent sensitive data from falling into the wrong hands. If a device goes missing, you can lock it to disable access or do a full wipe to delete all data.
- Restrict which apps are allowed and which are prohibited. An MDM lets you block non-compliant apps to reduce risks. You can also deploy mandatory apps for productivity or security.
- Apply software updates automatically to patch security holes and keep devices up to date. Outdated software and operating systems are common vulnerabilities that put data at risk.
- Monitor devices for signs of jailbreaking or rooting and other threats. An MDM provides visibility into the security posture and compliance of managed devices.
- Enforce location-based policies if a device leaves a specified geographic area. For example, you can disable access to work data or lock the device when it’s outside of the country.
- Require a PIN or passcode to be entered before company data can be accessed. This adds an extra layer of protection for your business information.
To get the most out of your MDM, enroll all company-owned and BYOD devices. And don’t forget to communicate your MDM policies to employees before they bring their devices on board.
Going Beyond MDM: The Need for Secure File Sharing
MDM solutions allow you to enforce policies like requiring strong passwords, remote wiping lost devices and restricting risky apps. However, they don’t actually protect the files and data on the devices themselves.
For stronger security, you can use a secure file-sharing solution. It’s like a digital vault for your files, keeping them encrypted and access-controlled, even when they’re accessed from mobile devices.
Here are a few of the key ways a secure file-sharing solution helps protect your data:
- Access to files on the go. Users can share and manage access to files from a mobile device without needing to store those files on the device.
- Access control. You determine who has access to files and can revoke access at any time (including for users who have had their device lost or stolen). Users can view, edit, copy or share files according to the permissions you set.
- Audit trails. Track file activities such as when a file was uploaded and by whom, and who has accessed files when.
- User authentication. Users must log in to the secure file-sharing app using strong, two-factor authentication. This verifies their identity and grants access to approved files.
Using an MDM solution in combination with a secure file-sharing solution that provides file-level security can help you protect your organization’s sensitive data in today’s mobile world. You get the device-level controls of MDM plus an encrypted, access-controlled environment for your most valuable digital assets.
Top 4 Features of a Secure File-Sharing Solution
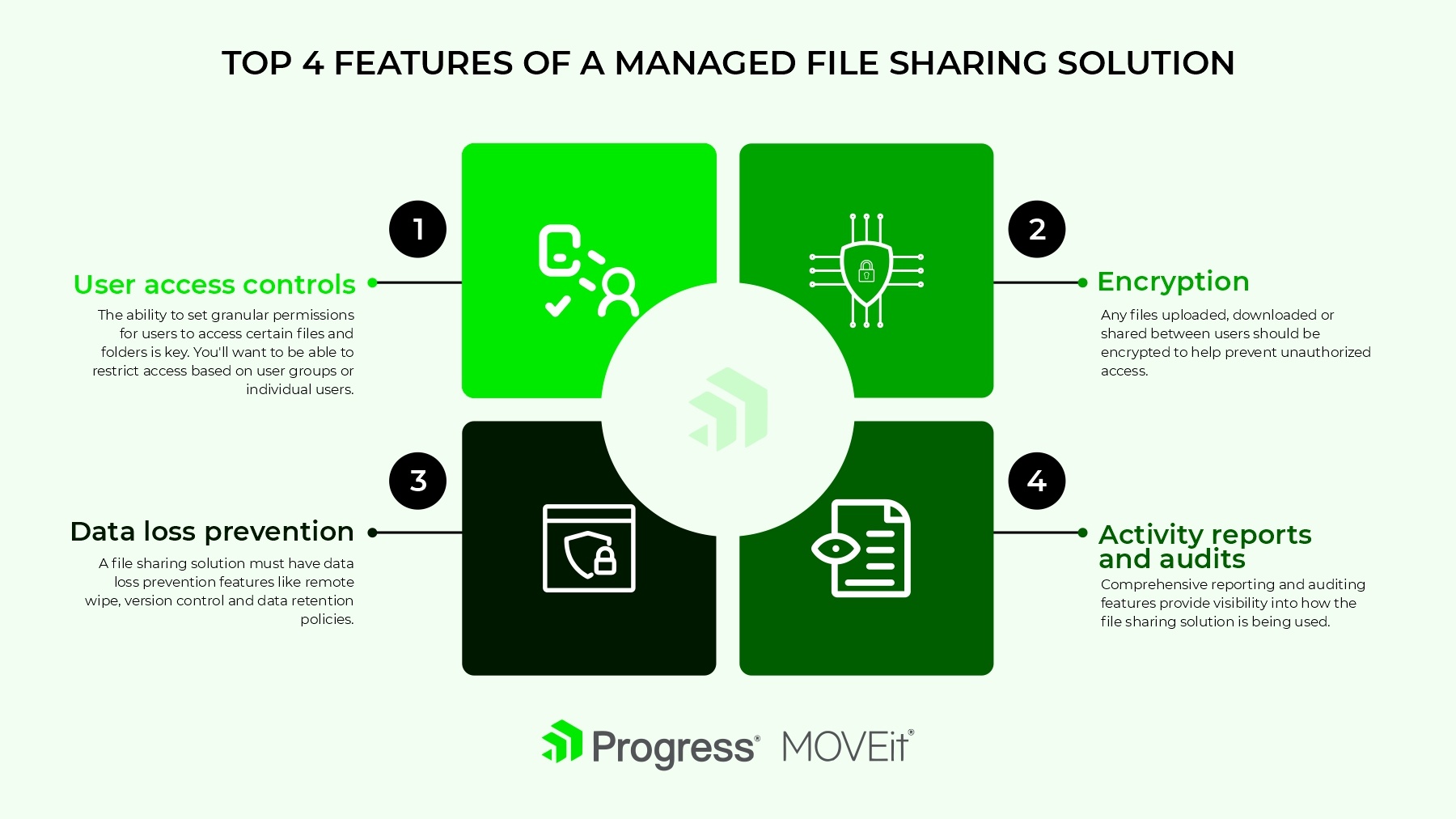
A secure file-sharing solution is essential for any business with mobile devices. Look for these top features to help you keep your data protected:
User Access Controls
The ability to set granular permissions for users to access certain files and folders is key. You’ll want to be able to restrict access based on user groups or individual users. Make sure administrators can audit user activity to monitor for any unauthorized access.
Encryption
Any files uploaded, downloaded or shared between users should be encrypted to better prevent unauthorized access. AES 256-bit encryption is currently the industry standard. Data should remain encrypted even while at rest on servers.
Data Loss Prevention
A secure file-sharing solution must have data loss prevention features like remote wipe, version control and data retention policies. This allows admins to remotely delete files from lost or stolen devices, revert to previous file versions if needed and set policies to automatically delete files after a certain amount of time.
Activity Reports and Audits
Reporting and auditing features provide visibility into how the file-sharing solution is being used. Reports should show details like users logging in, files accessed, downloads, uploads, shares and more. Audits give a historical look at all user and administrator activity for compliance and monitoring purposes.
Training Employees on Mobile Security
Employees are the frontline of any organization’s cyber defenses, yet they are also the weakest link and the most vulnerable access point. According to IBM, over 95% of successful data breaches are due to human error. This sobering statistic highlights why mobile security training is so critical.
Mobile security training should:
- Educate staff about the risks of unsecured Wi-Fi networks. Public networks are a hotbed for man-in-the-middle attacks that can expose login credentials and sensitive data.
- Train employees to enable password protection, encryption and remote wipe capabilities on all mobile devices. These precautions can help thwart thieves if a device is lost or stolen.
- Issue regular phishing simulation tests to make security awareness a habit.
- Provide resources for learning about new threats like malware, ransomware and social engineering.
Try Progress MOVEit
Progress MOVEit is a secure managed file transfer solution that helps organizations better protect files accessed from mobile devices. It requires user authentication and provides a comprehensive audit trail. See how it could fit into your security strategy:

